Overview:
This document provides a comprehensive guide for resetting passwords and SSH keys on EC2 instances using AWS Systems Manager (SSM). It outlines step-by-step instructions to ensure a seamless and secure process for managing access credentials across multiple instances.
Change ssh key of instance
Ensure Prerequisites:
Ensure that the IAM role associated with your EC2 instances has permissions to execute SSM commands
- Check EC2 Instance IAM Role:
- Go to the Amazon EC2 console: EC2 Console.
- Navigate to the “Instances” section in the left navigation pane.
- Select the EC2 instance for which you want to check the IAM role.
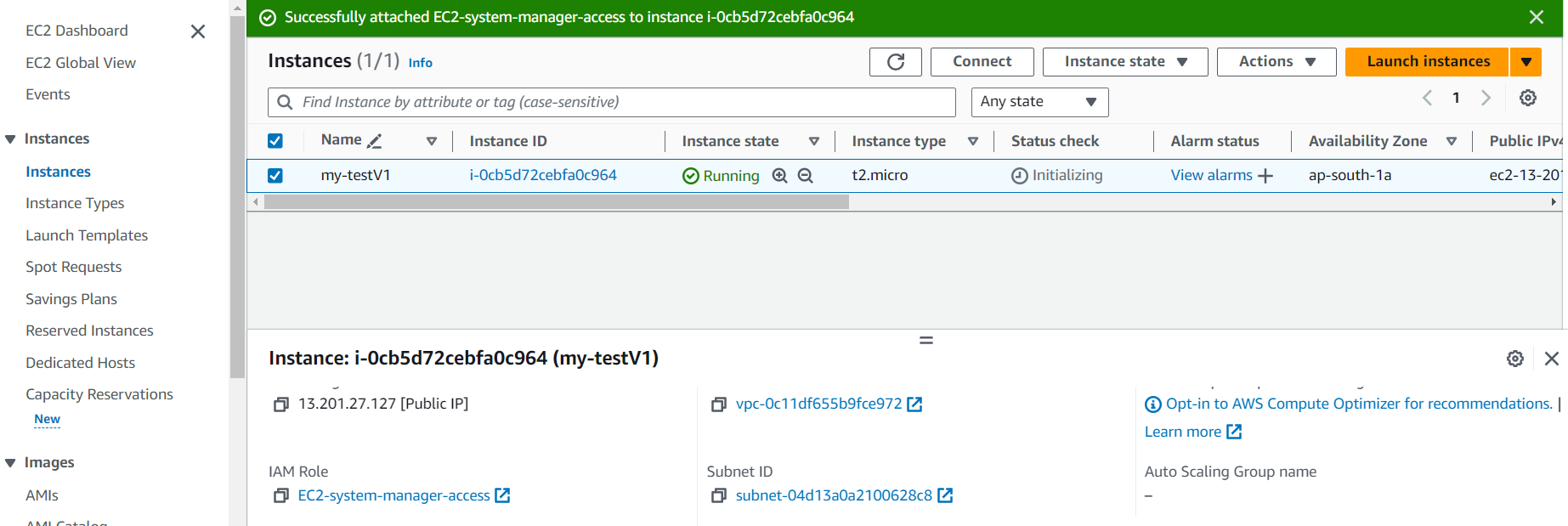
2. Navigate to the IAM Role:
- In the details pane at the bottom, locate the “IAM role” associated with the selected EC2 instance.
- Click on the IAM role name. This will open a new tab or window in your browser, redirecting you to the IAM console.
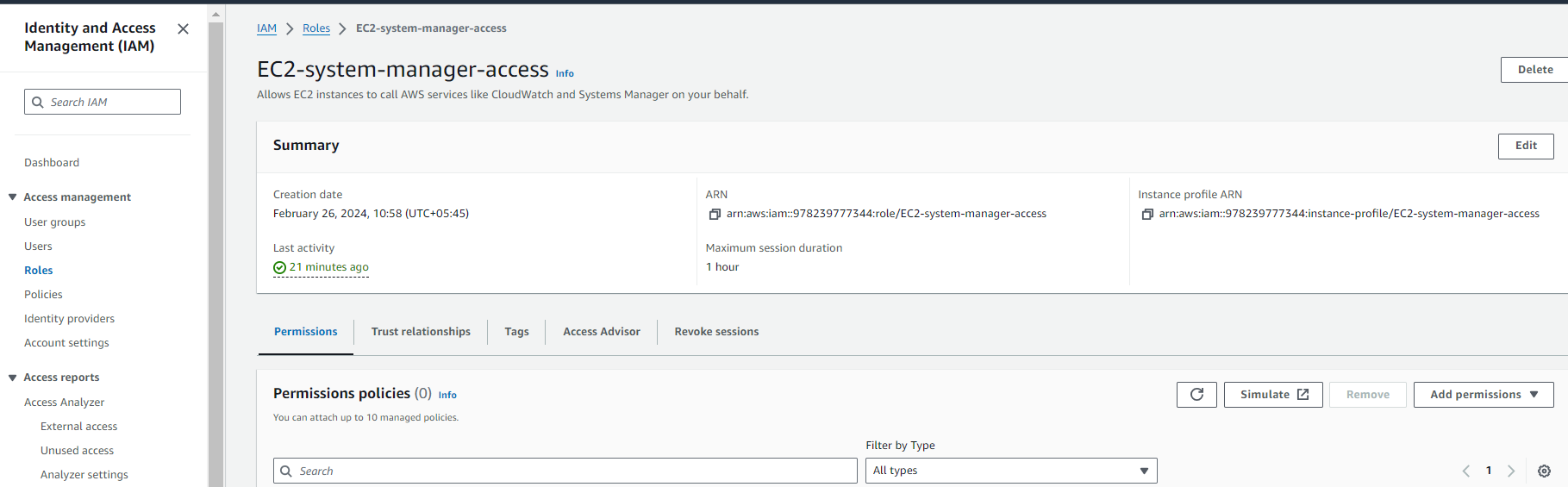
3. Add Permissions to the IAM Role:
- In the IAM console, you’ll see the permissions attached to the IAM role.
- Click on the “Add permissions” button to add new permissions to the role.
- Choose the appropriate permissions policy or create a custom policy that grants the necessary permissions to execute SSM commands.
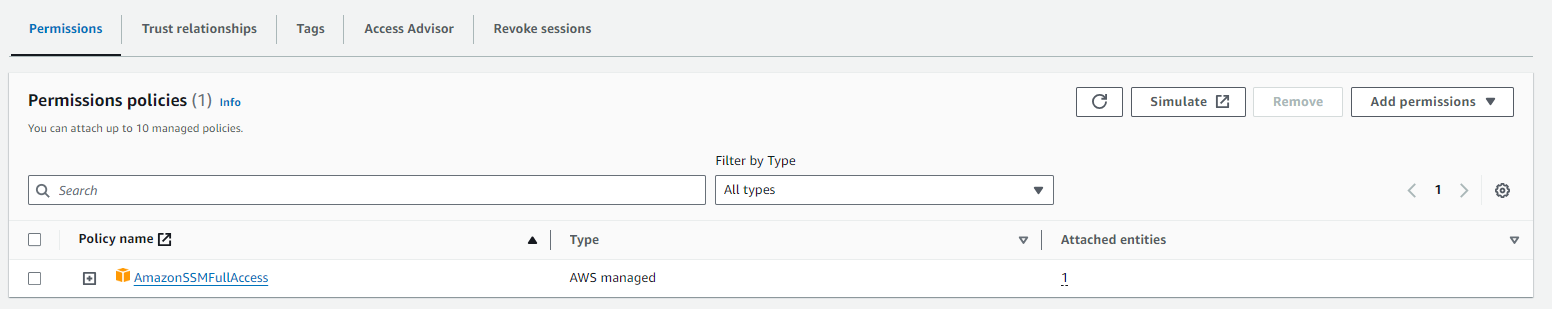
- To grant permissions to execute SSM commands, you can attach the “AmazonSSMFullAccess” managed policy, which provides the required permissions for Systems Manager.
Generate a New SSH Key Pair (Optional):
You can generate a new SSH key pair using either your local machine or AWS Key Pairs:
Option 1: Generate Locally:
- Open a terminal or command prompt.
- Run: ssh-keygen -b 4096 -f my-instance1-key
- Follow the prompts to set a passphrase or leave it blank.
- Copy the content of my-key.pub.
Option 2: Generate from AWS Key Pair:
- Navigate to EC2 dashboard > Key Pairs.
- Create a new key pair.
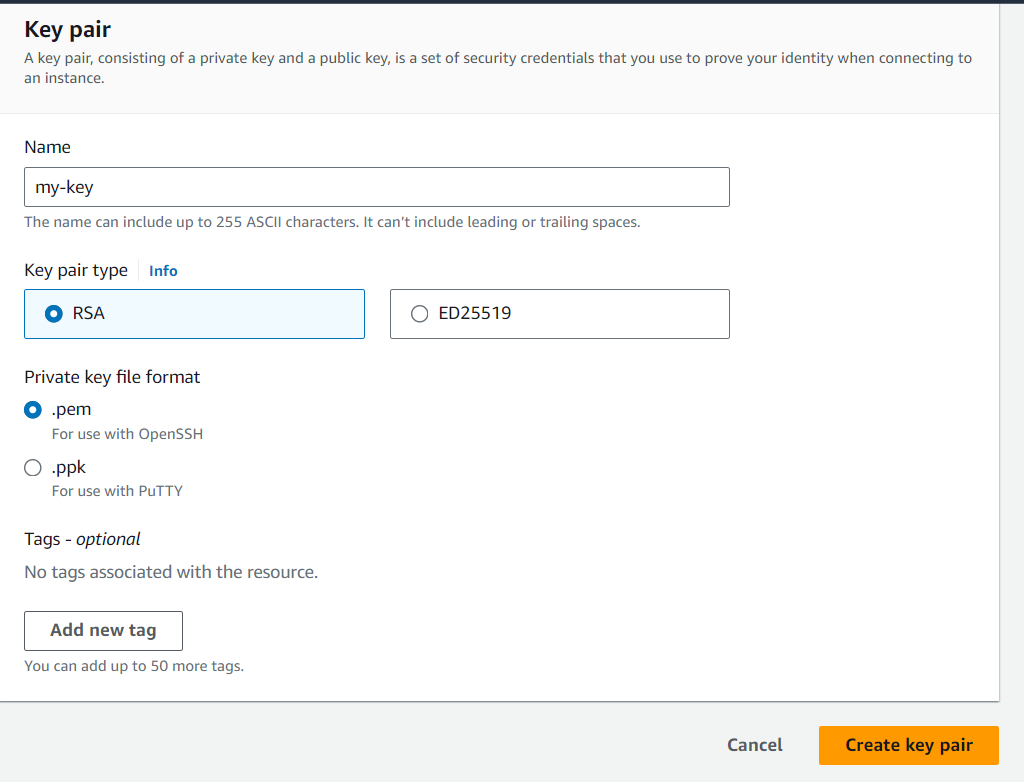
- Download the private key (my-key.pem).
- Run: ssh-keygen -y -f my-key.pem > my-key.pub
- Copy the content of my-key.pub.
- By following these steps, you can generate a new SSH key pair and obtain the public key for updating SSH keys on your EC2 instances.
Update SSH Authorized_keys using SSM Run Command:
Step 1: Navigate to the AWS Systems Manager console: AWS Systems Manager Console.
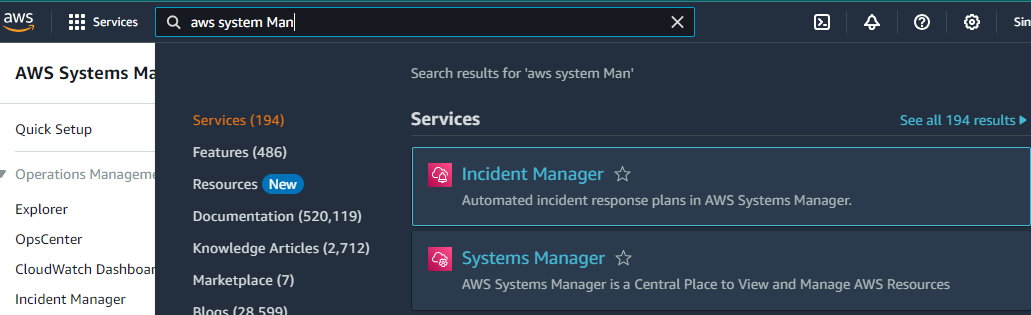
Step 2: Go to “Run Command” in the left navigation pane.
Step 3: Click on “Run Command” and then select “Run a command”.
Step 4: Choose the AWS-RunShellScript document
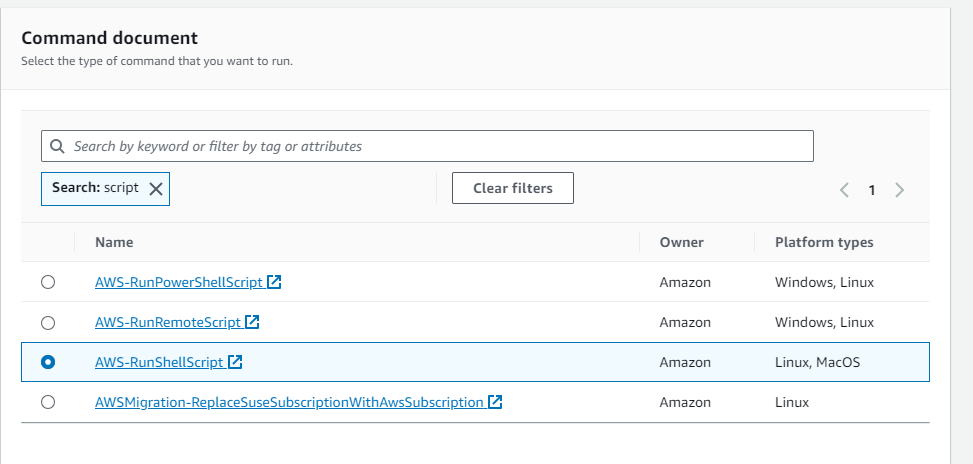
Step 5: In the “Targets” section, choose “Select instances manually”
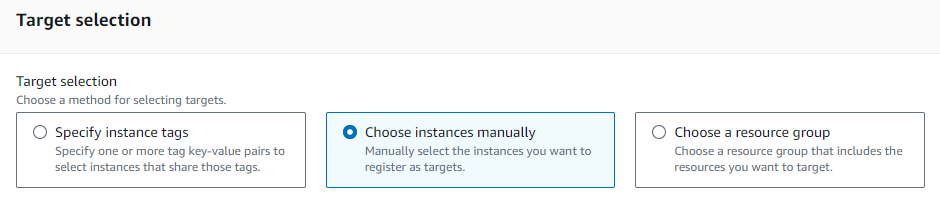
Step 6: Select the instances on which you want to update the SSH keys.
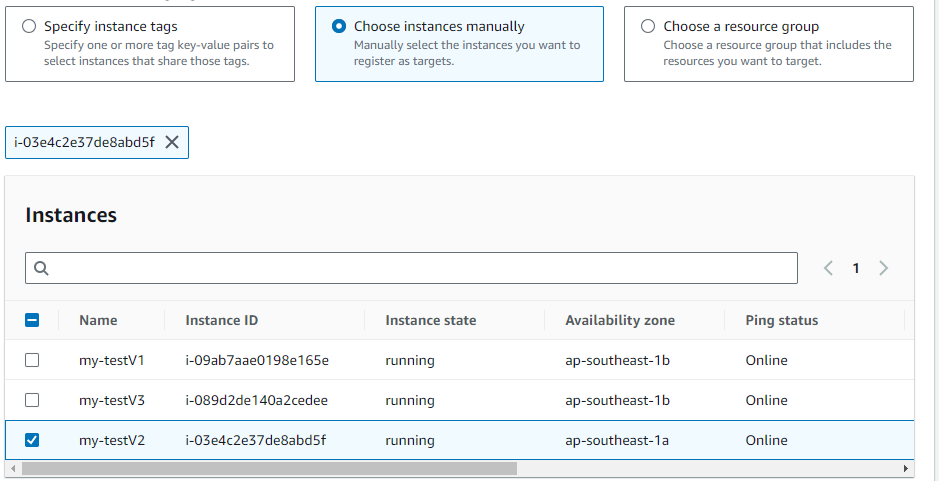
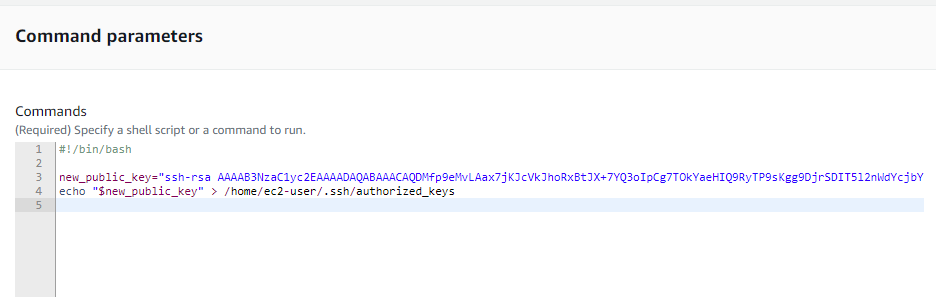
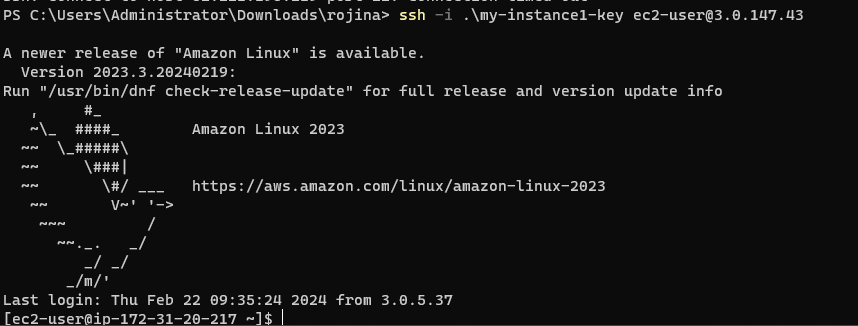
Step 7 : In the “Commands” section, paste the following command:
#!/bin/bash
new_public_key=”SSH key”
echo “$new_public_key” > /home/ec2-user/.ssh/authorized_keys
Replace SSH key with your actual new SSH public key
Step 8: Click on “Run”.
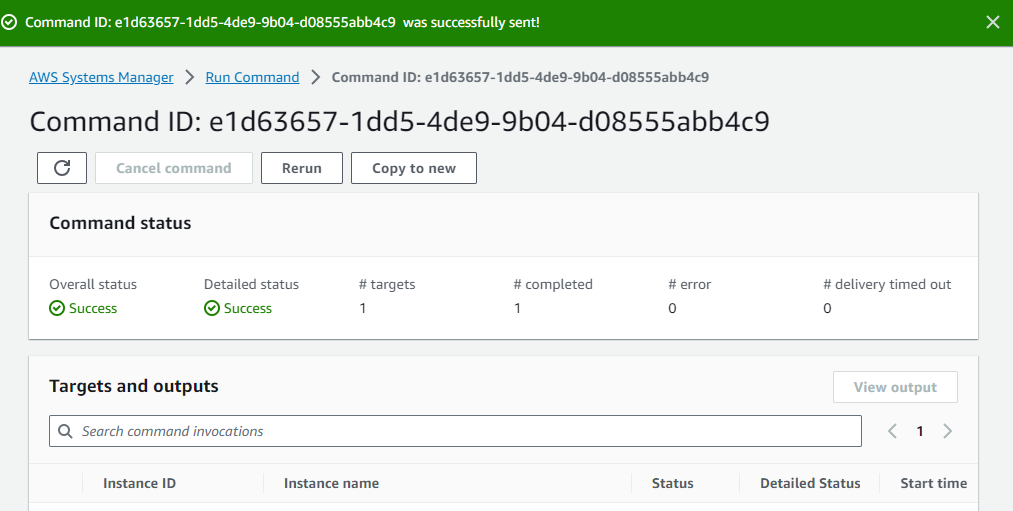
Wait for some second to success status.
Verify the Changes:
- After the command execution completes, verify that the SSH keys have been updated on each EC2 instance.
- You can attempt to SSH into each instance using the new SSH key to ensure that access is successful.
Changing Passwords for Multiple Users on EC2 Instances:
Execute the Script Using AWS Systems Manager:
Step 1: Follow the previous instructions to navigate to the AWS Systems Manager console and select “Run Command”.
Step 2: Choose the AWS-RunShellScript document.
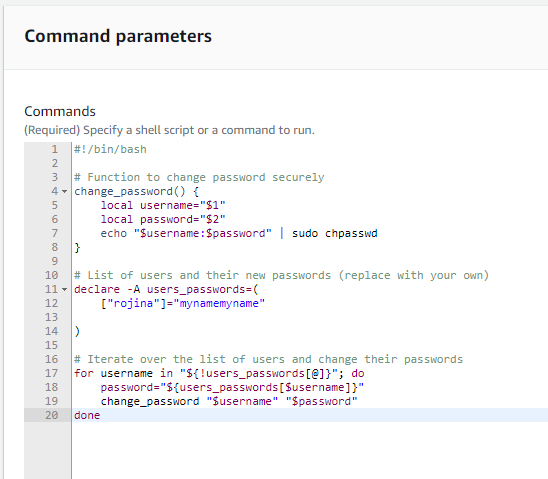
Step 3: Paste the script into the “Commands” section.
#!/bin/bash
# Function to change password securely
change_password() {
local username=”$1″
local password=”$2″
echo “$username:$password” | sudo chpasswd
}
# List of users and their new passwords (replace with your own)
declare -A users_passwords=(
[“user1″]=”new_password1”
[“user2″]=”new_password2”
)
# Iterate over the list of users and change their passwords
for username in “${!users_passwords[@]}”; do
password=”${users_passwords[$username]}”
change_password “$username” “$password”
done
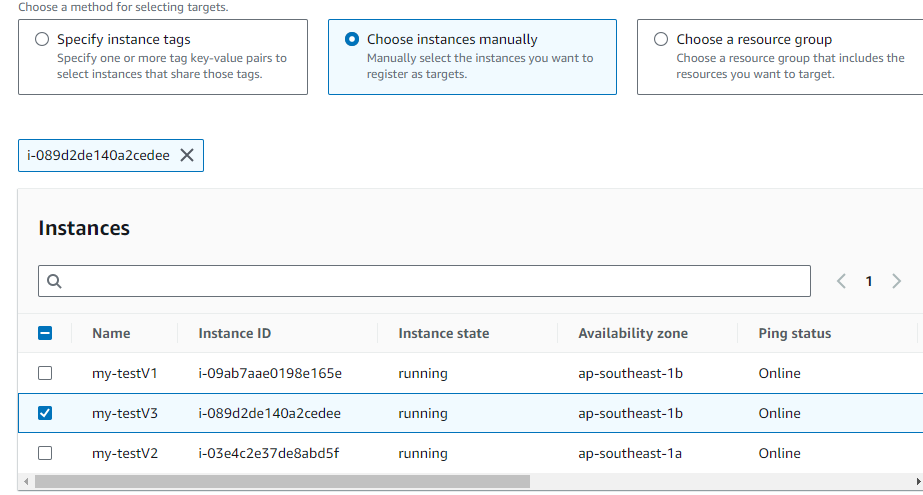
Step 4: Select the instances on which you want to change the passwords.
Step 5: Click on “Run”.
Verify Password Changes:
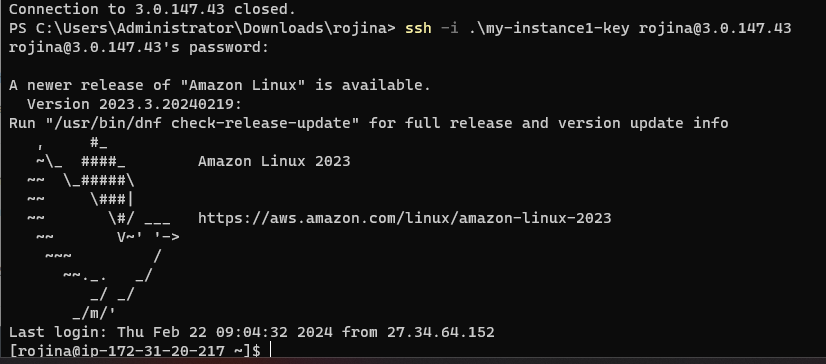
- After the command execution completes, verify that the passwords have been changed for the specified users on each EC2 instance.
- You may attempt to log in to each instance using the new passwords to ensure that access is successful.
 Finland
Finland Bangladesh
Bangladesh
