Genese Managed Cloud Security Threat Detection and Monitoring
Centralize security alerts, detect deviations from best practices, and maintain cloud security with automated checks for compliance (CIS, PCI DSS, NIST CSF, and more)
Genese Managed Cloud Security Threat Detection and Monitoring helps to detect and assess high-priority security alerts and security posture across all of your accounts and regions. This solution performs security best practice checks, aggregates alerts, enables automated remediation and consolidates, manages, and analyses log files from various sources, such as audit logs for access, configuration changes, and billing events. We utilise the Security Orchestration Automation and Response (SOAR) framework to automate and orchestrate security tasks and workflows to provide a top-to-bottom threat management system in your organisation.
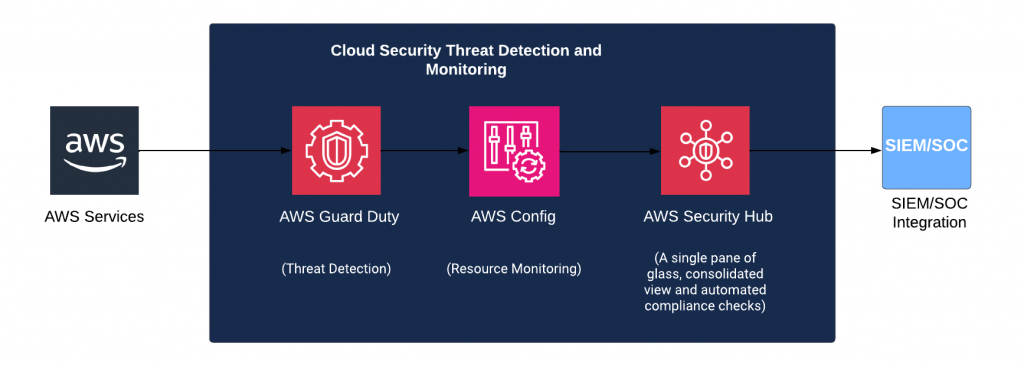
What Does Genese Managed Cloud Security Threat Detection and Monitoring Offer?
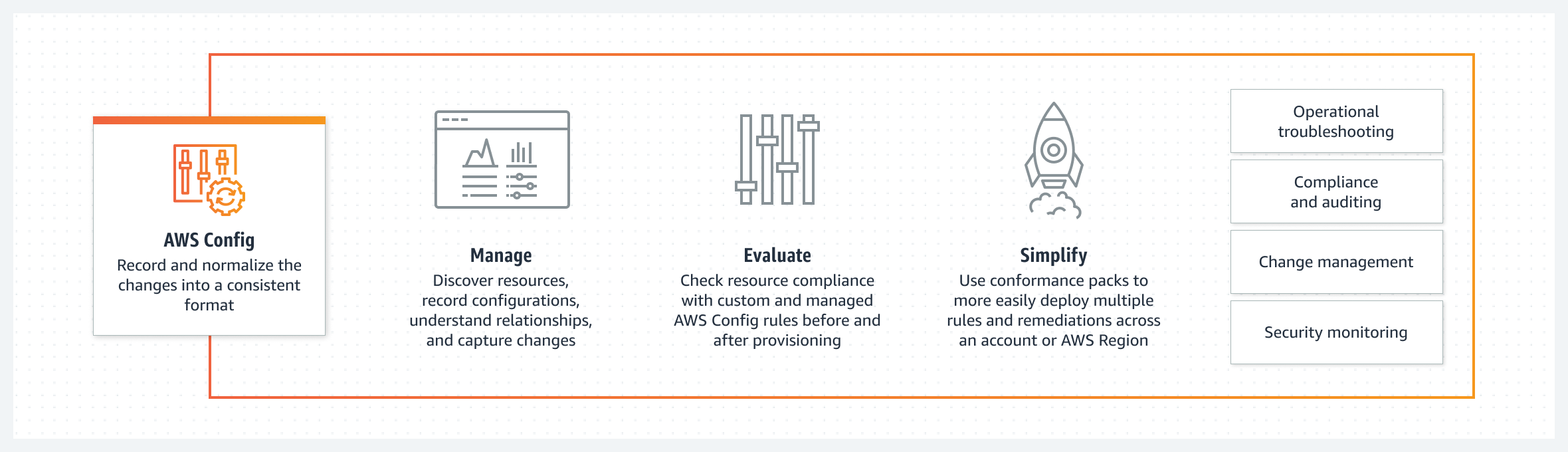
Configuration Tool
Configuration tool is used to continually assess, monitor, and record resource configuration changes to simplify change management. It can be utilised to audit and evaluate compliance of your resource configurations with your organisation’s policies on a continual basis. You can simplify operational troubleshooting by correlating configuration changes to particular events in your account.
Use Cases of AWS Config
1. Reduction of time-consuming actions: Our solution drastically reduces the false positives, repetitive tasks and manual processes that eat up security analysts’ time.
2. Streamline operational troubleshooting and change management: Discover resources that exist in your account or publish the configuration data of third-party resources into AWS Config, record their configurations, and capture any changes to troubleshoot operational issues quickly.
3. Deploy a compliance-as-code framework: Codify your compliance requirements as AWS Config rules and author remediation actions, automating the assessment of your resource configurations across your organisation.
4. Continually audit security monitoring and analysis: Evaluate resource configurations for potential vulnerabilities and review your configuration history after potential incidents to examine your security posture.
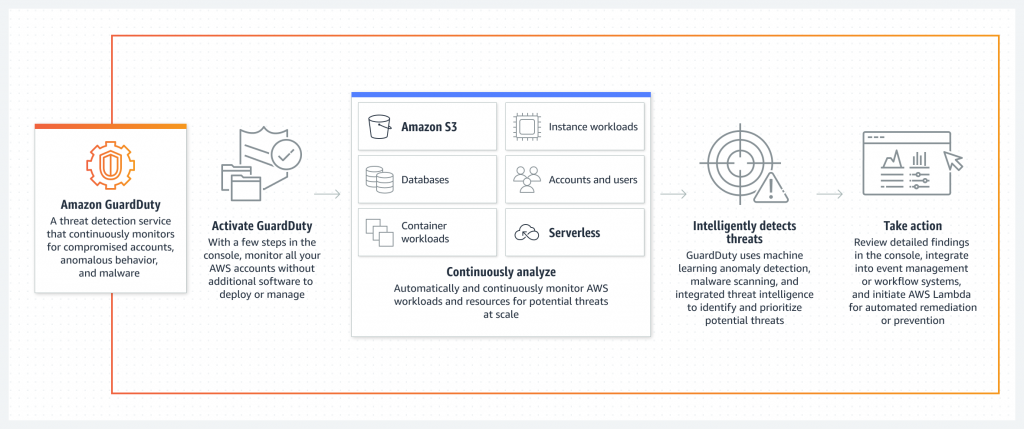
Threat Detection Tool
Utilise our threat detection service to continuously monitor your AWS accounts, instances, serverless and container workloads, users, databases, and storage for potential threats. Expose threats quickly using anomaly detection, machine learning, behavioural modelling, and threat intelligence feeds from AWS and leading third parties. Mitigate threats early by initiating automated responses and easily scale threat detection across your environment.
Use Cases of AWS Guard Duty
1. Improve security operations visibility: Gain insight into compromised credentials, unusual data access in Amazon Simple Storage Service (S3), suspicious logins in Amazon Aurora, and API calls from known malicious IP addresses.
2. Assist analysts in investigations and automate remediation: Receive findings with context, metadata, and impacted resource details. Determine the root cause with Amazon Detective. Route findings to AWS Security Hub and Amazon EventBridge.
3. Identify files containing malware: Scan Amazon Elastic Block Store (EBS) for files that might have malware creating suspicious behaviour on instance and container workloads running on Amazon Elastic Compute Cloud (EC2).
3. Cloud security posture management (CSPM): Cloud security posture management (CSPM) is designed to identify misconfiguration issues and compliance risks in the cloud. CSPM helps continuously monitor cloud infrastructure for gaps in security policy enforcement.
- Integrate multiple security solutions: It helps integrate security, IT operations and threat intelligence tools. You can connect all your different security solutions – even tools from different vendors – to achieve a more comprehensive level of data collection and analysis. Security teams can stop juggling a variety of different consoles and tools.
- Save time and money by simplifying integrations: Simplify and streamline data ingestion into your Security Information and Event Management (SIEM), ticketing, and other tools by consolidating the integrations between AWS services and your downstream tooling and normalising your findings.
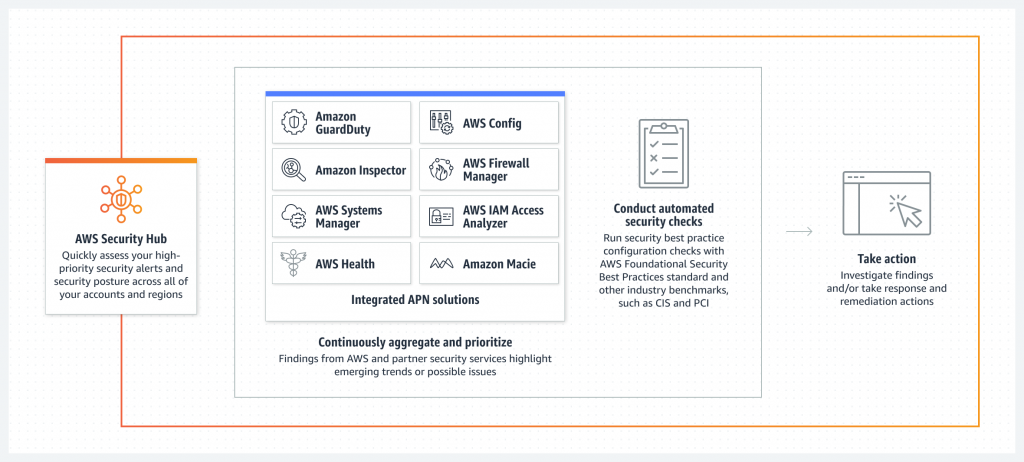
- One-stop comprehensive view: Our solution allows you to view everything in one place. Your security team gains access to a single console that provides all the information it needs to investigate and remediate incidents. Security teams can go to one place to access the information they need.
- Conduct cloud security posture management (CSPM): Reduce your risk with automated checks based on a collection of security controls curated by experts and simplify compliance management with built-in mapping capabilities for common frameworks like CIS, PCI DSS, and more.
- Accelerated incident response: Reduce both the mean time to detect (MTTD) and the mean time to respond (MTTR) with our solution. Because many actions are automated, a large percentage of incidents can be dealt with immediately and automatically.
- Access to high-quality threat intelligence: Aggregate and validate data from threat intelligence platforms, firewalls, intrusion detection systems, SIEMs and other technologies, offering your security team greater insight and context. This makes it easier to resolve issues and improve practices. Analysts are better able to conduct deeper and broader investigations when problems arise.
- Enhanced reporting and communication: With all security operations activities aggregated in one place and displayed in intuitive dashboards, stakeholders can receive all the information they need, including clear metrics that help them identify how to make improvements to workflows and reduce response times.
- Initiate Security Orchestration, Automation, and Response (SOAR) workflows: Automatically enrich findings, remediate them, or send them to ticketing systems with Security Hub’s integration with EventBridge.
- Boosts decision-making ability: Our SOAR platform aims to be user-friendly, even for less experienced security analysts, by offering features like pre-built playbooks, drag-and-drop functions to build playbooks from scratch, and automated alert prioritisation. Additionally, our SOAR tool can gather data and offer insights that make it easier for analysts to evaluate incidents and take corrective actions to remediate them.
- Correlate your security findings to discover new insights: Better prioritise the response and remediation efforts of your central security teams and DevSecOps teams by searching, correlating, and aggregating diverse security findings by accounts and resources.
Primary Services
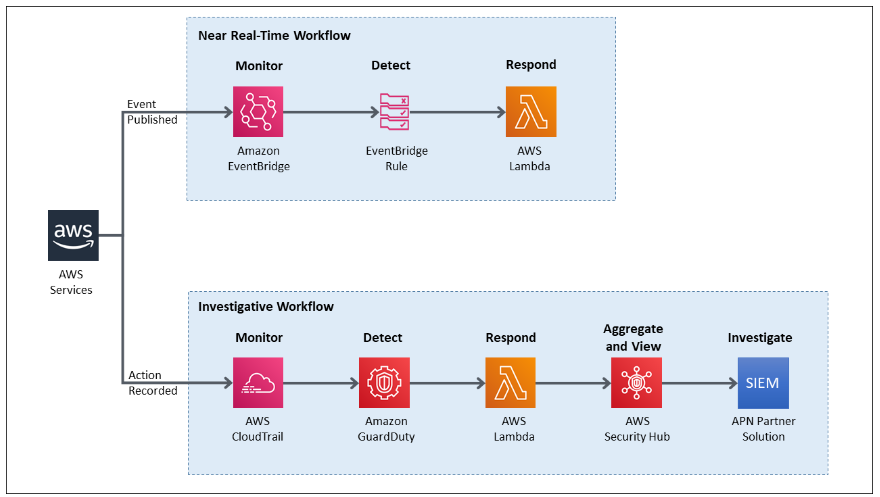
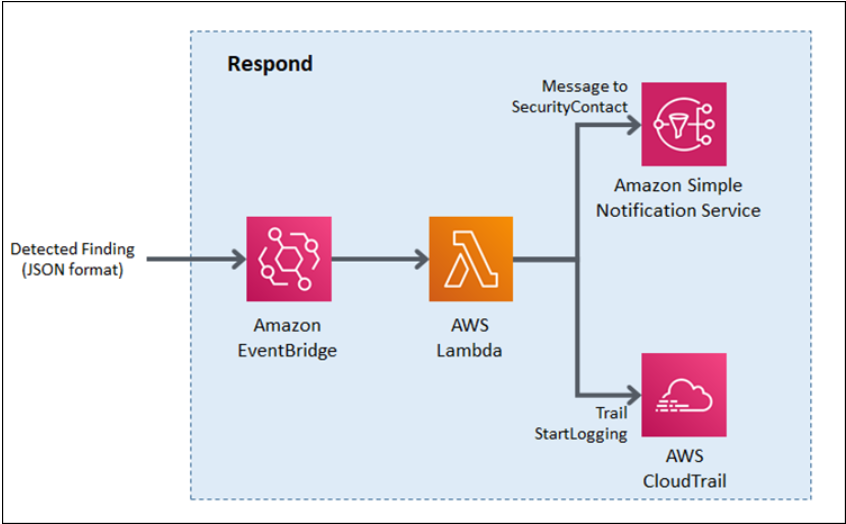
4. Log aggregation and central visibility : Log aggregation breaks down organisational silos and improves visibility by enabling multiple teams to access the same data in a centralised platform. Once logs have been aggregated, teams can generate metrics from log attributes in order to visualise long-term trends and alert on log data.
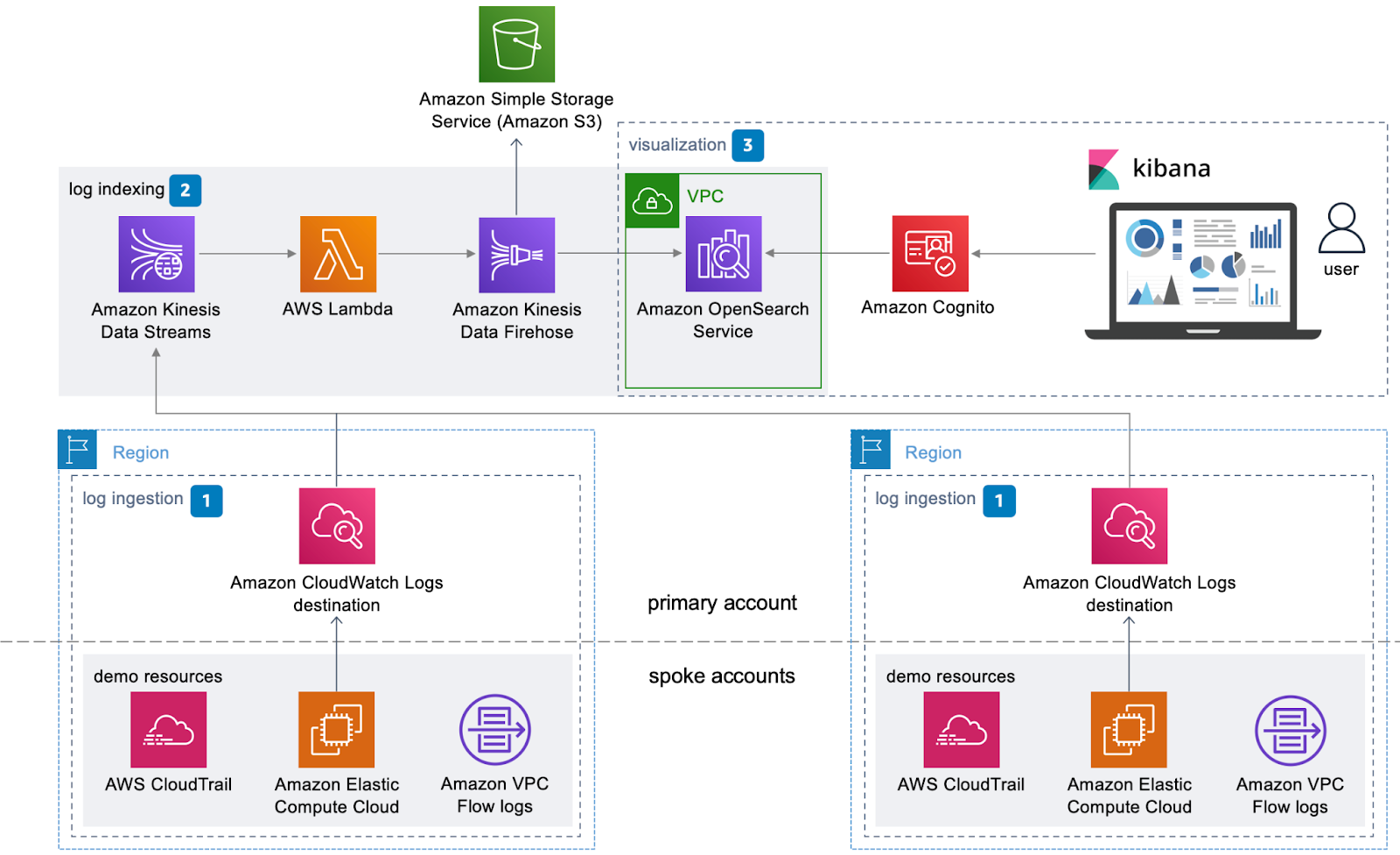
Use cases of centralised logging on AWS
- Use this solution out-of-the-box, or build and customise: The AWS CloudFormation template automatically launches and configures the components necessary to upload log files from multiple accounts and AWS Regions to Amazon OpenSearch Service for analysis and visualisation in a customizable, user-friendly dashboard.
- Access to your dashboards using Amazon Cognito: Control access to your dashboards using Amazon Cognito to simplify authentication to Amazon OpenSearch Service.
- Logging capabilities beyond default AWS service logs: Extend your logging capabilities beyond default AWS service logs. This flexible solution includes examples for capturing host-level log files and VPC flow logs and is designed to scale with your growing business.
- Data visualisation using built-in Amazon OpenSearch Service support: Simplify data visualisation using built-in Amazon OpenSearch Service support for Kibana, including a default set of preconfigured dashboards that give you a first glimpse into the customization capabilities of Kibana.
Who uses Genese Managed Web Application Security?
Banking and Financial Institutions (BFIs)
Content Management Systems (CMS) Providers
E-commerce Platforms
Security Service Providers

Government Organizations
Why us?
AWS Expertise
Compliance
Complete team integration
Efficiency
Contact Us
Please fill out the form; one of our experts will connect with you soon.
 Finland
Finland Bangladesh
Bangladesh