AWS Key Management Service (KMS)
AWS Key Management Service (KMS) is a managed solution designed to empower businesses with robust control over their cryptographic keys, ensuring the security and encryption of their data. It offers comprehensive key storage, administration, and auditing capabilities, enabling enterprises to seamlessly manage encryption across all AWS services.
Overview
AWS Key Management Service (KMS) is a managed service that enables businesses to generate, manage, and exercise control over the cryptographic keys that safeguard and encrypt their data. An excellent key storage, administration, and auditing solution is provided by AWS KMS to enterprises, enabling them to easily regulate the encryption of data stored across all AWS services.
AWS KMS, as its name implies, is a key management and encryption service that has been scaled for usage in the AWS cloud. Employing AWS KMS’s encryption keys and features, businesses may secure data across all AWS-based applications. Data keys that are not limited to AWS KMS can also be generated using the service. AWS KMS may be used to produce both symmetric and asymmetric KMS keys for encryption and signing.

Key Features of AWS Key Management Service (KMS)
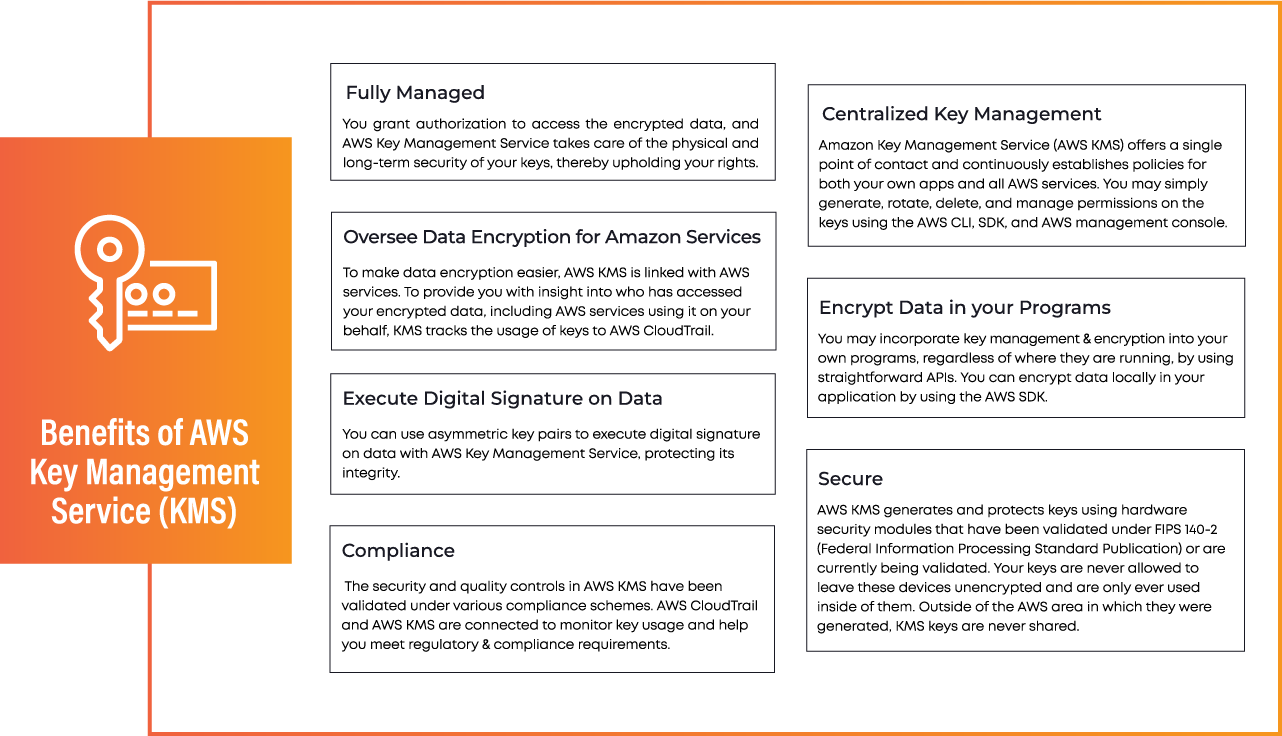
Centralized Key Management
The keys that encrypt your data can be centrally managed with AWS KMS. This implies that setting up and maintaining your own key management infrastructure is not something you need to worry about.

Integration with AWS Services
Amazon S3, Amazon RDS, Amazon Redshift, Amazon EBS, and many more AWS services are easily integrated with KMS. This gives you the option to use KMS-managed keys to encrypt the data that is stored in these services.
Granular Access Control
To regulate who can use which keys and under what circumstances, you can create fine-grained access policies using AWS KMS. This guarantees that encrypted data can only be accessed by authorized users and services.
Hardware Security Modules (HSMs)
To safeguard the security of your keys, AWS KMS makes use of HSMs. Hardware-specific modules called HSMs are made specifically to handle and store cryptographic keys safely.

Key Usage Auditing
KMS offers thorough key usage logging that includes the user’s name, key usage date, and time of use. In addition to helping you comply with regulations, this keeps an eye out for any unwanted access to your keys.

Automatic Key Rotation
By automatically switching out old keys for new ones on a regular basis, KMS’s automatic key rotation feature improves security. This lowers the risk that comes with having long-lasting keys.

Integration with AWS CloudTrail
All KMS API calls can be logged using AWS CloudTrail, which offers a thorough audit record of key management operations.
How does it Work?
AWS KMS keys can be created using AWS CloudFormation templates, the CreateKey operation, or the AWS Management Console. During the creation process, select the KMS key type, regionality (single or multi-region), and key material source (default is AWS KMS). These attributes cannot be changed once the key is created. Setting and managing the KMS key policy is also required.
For encrypting data in AWS services, create a symmetric encryption KMS key, as these services support only symmetric keys. For assistance in choosing a key type, refer to the “Selecting a KMS key type” guide.
An alias (friendly name) must be assigned to a KMS key created in the AWS KMS console. The CreateKey method does not set an alias, so use the CreateAlias procedure to create an alias for a new or existing KMS key.
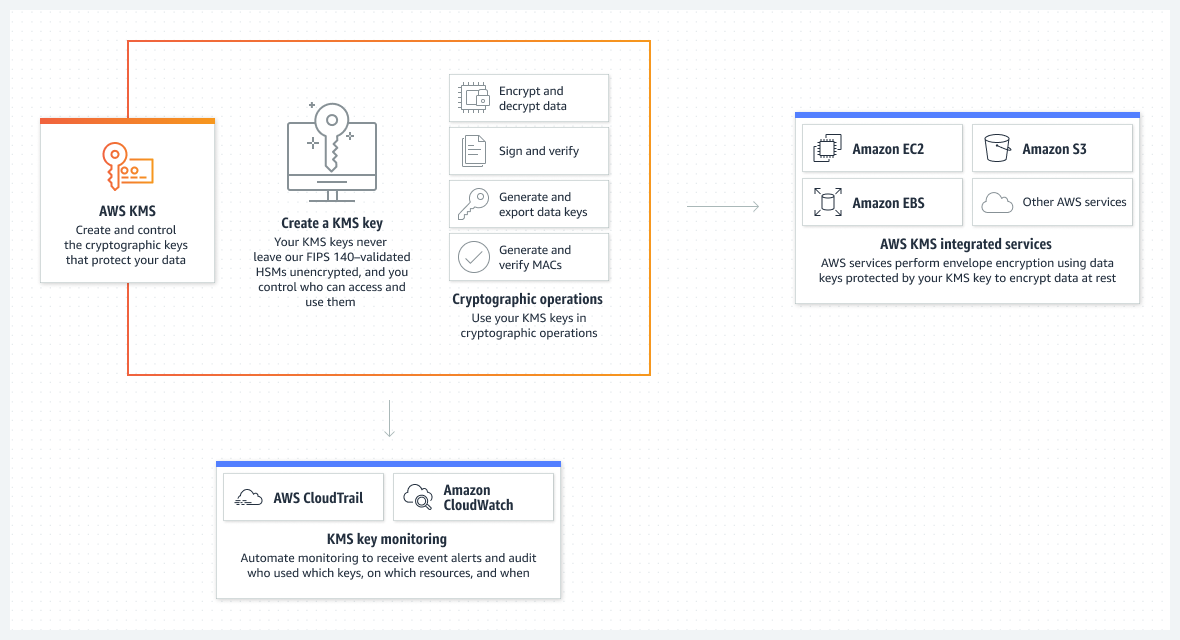
Integrations with AWS KMS
Almost all AWS services that encrypt corporate data are compatible with AWS KMS. Data is encrypted using only symmetric encryption KMS keys by all AWS services linked with AWS KMS. They are not compatible with asymmetric KMS key encryption. Businesses can utilize the AWS KMS keys in their account to secure the data that their AWS services receive, store, or control when they integrate them with AWS KMS.
To record an organization’s usage of its KMS keys for auditing, legal, and compliance needs, AWS KMS interfaces with AWS CloudTrail. Log files from CloudTrail are delivered to the organization’s Amazon S3 bucket, where they can be used for key use audits.
The following are a few additional potential AWS KMS integrations:
- Amazon DynamoDB
- Amazon EBS
- Amazon EMR
- Amazon RedShift
- Amazon RDS
- Amazon S3
- WorkSpaces
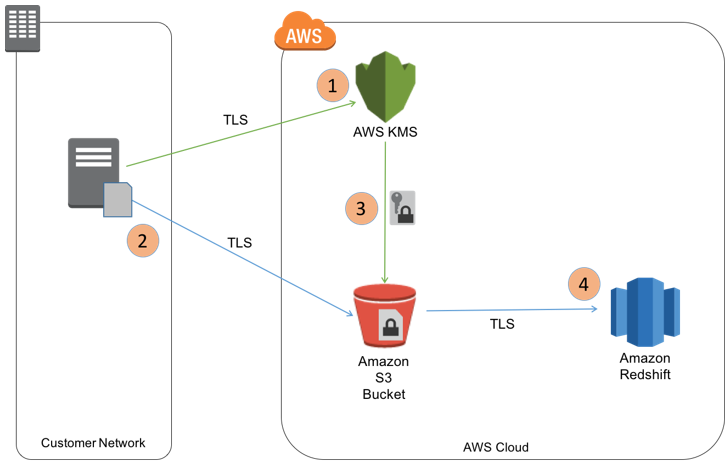
Fig: Encrypting and integrating Amazon Redshift Loads with AWS KMS and Amazon S3
Envelope encryption in AWS KMS
AWS KMS employs Envelope encryption, which requires two distinct keys for encryption and data protection. In this procedure, plaintext data is encrypted using a data key, then the data key is subsequently encrypted using a different key. The root key, sometimes referred to as the Amazon KMS key, is the top-level plaintext key-encryption key that is needed to decrypt the keys and data. AWS KMS securely stores and manages all encryption keys. The AWS KMS FIPS verified HSM never lets root keys out unencrypted.
Users can safely store the encrypted data key alongside their encrypted data since envelope encryption protects data keys. Additionally, it saves them from having to repeatedly encrypt raw data with different keys by enabling them to re-encrypt only the data keys that safeguard the raw data. Furthermore, envelope encryption combines the benefits of public key algorithms, which streamline key management and enable intrinsic role separation, with symmetric key algorithms, which are quicker and result in smaller ciphertexts.
Benefits of AWS Key Management Service (KMS)
Verification of compliance for AWS KMS
The security and compliance of AWS KMS are evaluated by independent auditors. The following compliance standards, which have validated and certified AWS KMS as of 2022, include:
SOC 1 report
SOC 2 report
SOC 2 report for confidentiality
PCI DSS Attestation of Compliance (AOC) and Responsibility Summary
FedRAMP-High
ISO27001:2013, 27017:2015, 27018:2014
Cloud Computing Compliance Controls Catalog (C5)
Pick Genese as an Advanced Tier Services Partner for your AWS needs

 Finland
Finland Bangladesh
Bangladesh