AWS Security Hub
“AWS Security Hub” is a comprehensive security service that provides users with a centralized view of their security posture across various AWS accounts. It aggregates, organizes, and prioritizes security findings from multiple AWS services such as “Amazon GuardDuty”, “Amazon Inspector”, and “Amazon Macie”, as well as from AWS Partner Network (APN) security solutions.
Key Features of AWS Security Hub
Aggregated Security Findings
AWS Security Hub consolidates security findings from multiple AWS services, enabling users to gain a holistic view of their security status.

Automated Compliance Checks
It automates continuous compliance checks against industry standards and best practices.

Proactive Threat Detection
Security Hub prioritizes findings based on severity, allowing users to focus on addressing the most critical issues first.
Integration with AWS Config
It integrates seamlessly with AWS Config, enabling users to assess their AWS resource configurations for compliance and security best practices.

Custom Actions
Users can define custom actions to remediate security findings directly from the Security Hub console or through automated workflows.
How does the Security Hub operate?
Security Hub makes it easier to analyze and enhance your security posture by automating security best practice tests powered by AWS Config rules and integrating with dozens of AWS services and partner products. However, Security Hub only detects and aggregates results generated once you enable it.
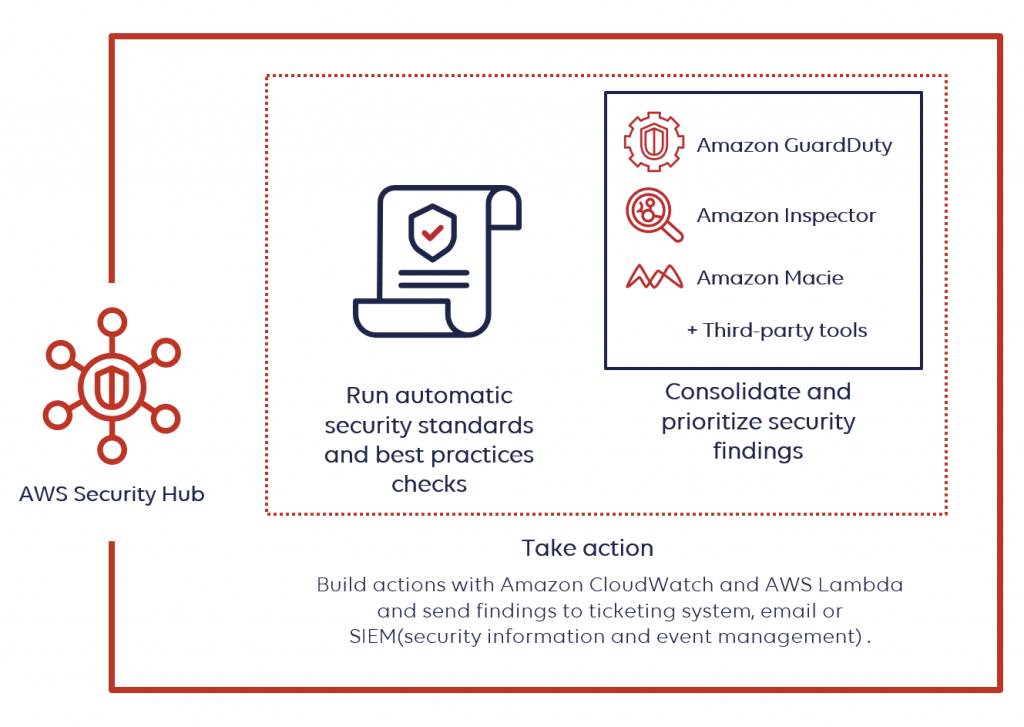
Integration of Security Hub
AWS partners’ third-party products and a range of AWS services can be integrated with Security Hub. This is also one of the primary advantages, as typically you have to examine each service individually and look up its results.
Security Hub connects with all of the core AWS security technologies.
It works with the following AWS services:
- Amazon GuardDuty for risk-reduction tasks, data stored in Amazon S3, and intelligent continuous threat detection of your AWS accounts.
- You may use Amazon Macie to search for personally identifiable information in your S3 buckets, categorize sensitive data as high, medium, or low risk, and receive alerts based on the level of sensitivity.
- You can, of course, utilize Amazon Inspector to do routine vulnerability and exposure tests on Amazon EC2 instances.
- IAM Access Analyzer: It’s a tool that checks if the policies linked to your AWS resources—such as Lambda functions, S3 buckets, KMS keys, and identity access management roles—permit external access from outside of your AWS account.
- You can automate any response to the detected warnings by using AWS Lambda in conjunction with Amazon CloudWatch and CloudWatch events.
- AWS Firewall Manager is a solution that lets you manage security groups and web application firewalls across several AWS accounts in one place.
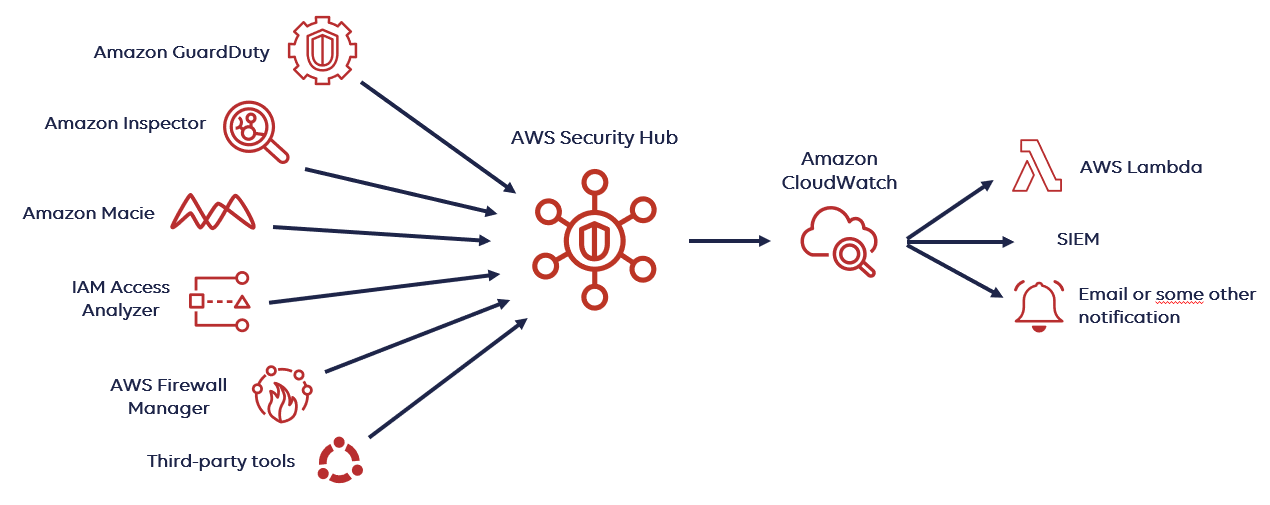
Integration of Third-party tools with Security Hub
Security HUB can also be integrated with numerous third-party tool integrations available. Integrated Amazon Partner Network (APN) security solutions is a page on the official AWS website that has a comprehensive list of them.
Available security guidelines and evaluations of best practices
You can select the security standard you want to employ when you enable AWS Security Hub. These security standards offer a set of checks and balances to assess adherence to legal frameworks and industry best practices.
- Amazon Basic Security Guidelines
AWS accounts and deployed resources that do not comply with security best practices are flagged by an automated security assessment system known as the AWS Foundational Security Best Practices standard. Experts in AWS security define the standard. This carefully chosen collection of controls enhances your AWS security posture and includes coverage for the most widely used and essential services.
- CIS Benchmark for AWS Security Hub
A benchmark containing broad security recommendations for AWS was released by the Center for Internet Security (CIS). By using a subset of CIS standards, this Security Hub standard automatically assesses your compliance readiness.
It consists of items such as:
- Steer clear of using the “root” account.
- Make sure the “root” account’s MFA is enabled.
- Make sure the IAM password policy mandates a minimum length of 14 characters.
- Make sure credentials that aren’t used for 90 days or more are disabled.
- Make sure that no security groups permit access to port 22 from 0.0.0.0/0.
- Verify that rotation is enabled for KMS keys created by customers.
- PCI DSS, or Payment Card Industry Data Security Standard
These are some guidelines that you must follow if you handle any kind of credit card transaction. They are all related to credit card payments. Further information is available in the official AWS documentation: PCI DSS.
Benefits of AWS Security Hub
Centralized Visibility
Gain a centralized view of security across multiple AWS accounts and regions, simplifying security management and compliance.
Streamlined Compliance
Automate compliance checks and streamline audit processes with predefined standards and best practices.

Proactive Threat Detection
Identify and prioritize security findings, allowing for timely detection and response to potential threats.
Scalability and Flexibility
Scale security operations according to business needs and customize security workflows to suit specific requirements.
Getting Started with AWS Security Hub
To start using AWS Security Hub, you need an AWS account. Once logged in to the AWS Management Console, navigate to the Security Hub service and follow the on-screen instructions to enable Security Hub for your AWS accounts. After enabling Security Hub, you can configure integrations with other AWS services and third-party solutions to begin receiving security findings and compliance checks. You can then use the Security Hub dashboard to view, prioritize, and manage security findings, as well as set up automated remediation actions for certain types of findings.
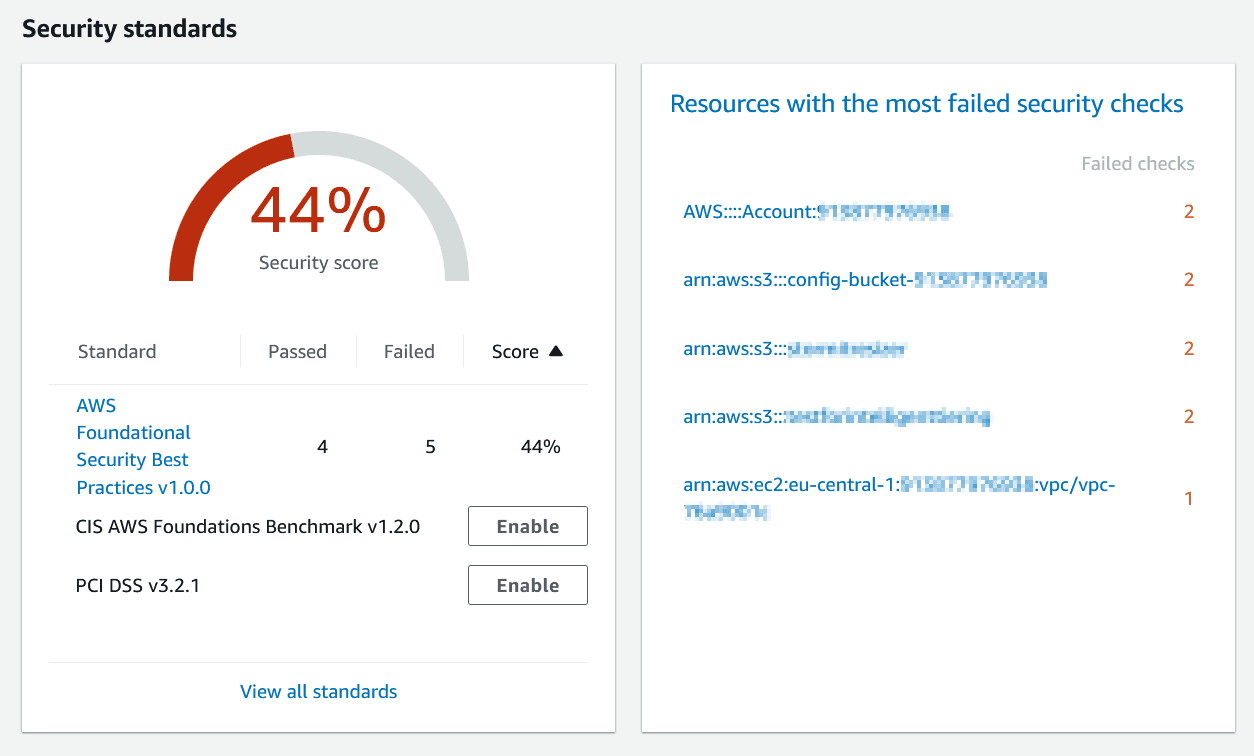
Insights on AWS Security HUB
It is also possible to develop insights in the Security Hub. An insight is formed when you utilize the Number by the filter to combine a set of findings. There are certain frequent security issues that may require insight-based solutions. You have the option to create your own original insights or select from Security Hub’s pre-existing managed insights.
Some of the Insights are as follows:
For your AWS environment, Security Hub offers a pre-built dashboard that can assist with organizing and prioritizing any issues or alarms found during security assessments.
This assists you in comparing your environment to industry best practices and requirements for AWS security. Additionally, you can benefit from the integrated automatic checks provided by CIS (Center for Internet Security) and PCI-DSS.
One can gain further Insights like:
- Public write or Read rights on Amazon S3 buckets
- S3 buckets containing private info
- The Amazon Machine Images (AMIs) producing the greatest results
- Principals at AWS exhibiting questionable access key behavior
- Amazon resources linked to improper use of resources
- Credentials missing security patches for significant vulnerabilities that may have been leaked from Amazon EC2 instances.
AWS Use Cases
World-renowned Enterprises have fortified their security systems through AWS Security HUB. Here are a few examples:
SIEMENS
Siemens strengthened security and enhanced Productivity using AWS Security HUB. Global technology company Siemens migrated to AWS Security Hub, improving productivity with a unified Security dashboard and automatic notifications while enhancing collaboration between teams.
SOUTHWEST AIRLINES
By using cloud-native elements for gathering security insights, the airline could focus on building innovative applications instead of managing infrastructure. As part of its ongoing migration to Amazon Web Services (AWS), Southwest adopted AWS Security Hub, which is a cloud security posture management service and is a key part of a broader automated and scalable integration that provides users with a comprehensive view of their security alerts and security posture across AWS accounts.
SWISS POST
SWISS POST chose AWS for its ‘Reliable Security’ factor. To ensure Project teams could focus on delivering business value, Swiss Post decided to ensure that every team had an AWS account baselined and compliant to Swiss Post security controls from day one. For monitoring, the Swiss Post security operations team uses AWS Security Hub in conjunction with the existing on-premises Splunk environment, to get an aggregated view of the whole dynamic account landscape.
BOTPRISE
Botprise was able to reduce its Time to Remediation by 86%, 34% reduction in operational costs on average using Automation and AWS Security Hub and achieved rapid customer growth. In 2022, Botprise pivoted to develop more cloud automation solutions with an increasing focus on security operation automation. During this pivot, Botprise received support from AWS, which Botprise used to gain momentum and grow by 400 percent in the security operations automation sector.
Pick Genese as an Advanced Tier Services Partner for your AWS needs

 Finland
Finland Bangladesh
Bangladesh