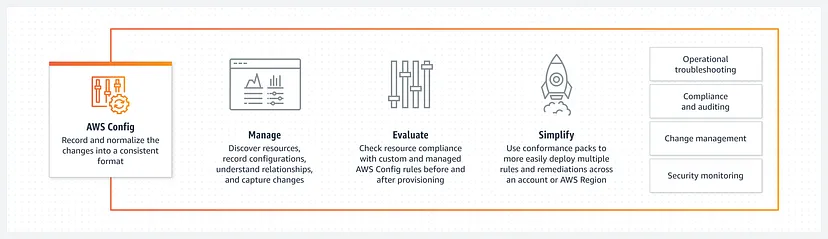
AWS Config provides a detailed view of your AWS resources, allowing you to see their configuration, relationships, and historical changes. This helps you understand how your resources are interrelated and how they’ve evolved, promoting better management and troubleshooting.
AWS Config is an AWS service that helps you track and manage your AWS resource configurations. You can use AWS Config to:
- Record changes to your AWS resources over time
- Evaluate the configuration of your AWS resources against your desired configurations
- Automate the remediation of non-compliant AWS resources
Enforcing security practices with AWS Config
You can use AWS Config to enforce security practices by:
- Creating AWS Config rules that check for non-compliant AWS resources
- Automating the remediation of non-compliant AWS resources
- Using AWS Config to monitor your AWS environment for security risks
Creating AWS Config rules
You can create AWS Config rules to check for various types of non-compliance, such as:
- IAM policies that grant excessive permissions
- S3 buckets that are not encrypted
- EC2 instances that are not running the latest security patches
You can configure AWS Config to automatically remediate non-compliant AWS resources. For example, you can configure AWS Config to automatically delete IAM policies that grant excessive permissions.
Monitoring your AWS environment with AWS Config
You can use AWS Config to monitor your AWS environment for security risks. For example, you can use AWS Config to track changes to your IAM policies, S3 buckets, and EC2 instances. You can also use AWS Config to create alerts for changes to your AWS resources.
Benefits of using AWS Config to enforce security practices
There are several benefits of using AWS Config to enforce security practices. Some of the benefits include:
- Improved security: AWS Config can help you to identify and remediate security risks so that you can reduce the risk of your AWS environment being compromised.
- Reduced costs: AWS Config can help you to automate the remediation of non-compliant AWS resources and to monitor your AWS environment for security risks so that you can save money.
- Increased compliance: AWS Config can help you to achieve compliance with various security standards, such as PCI DSS and HIPAA.
Conclusion
AWS Config is a valuable tool that can be used to enforce security practices. By using AWS Config, you can identify and remediate security risks, reduce costs, and achieve compliance with various security standards.
 Finland
Finland Bangladesh
Bangladesh
