Unveiling the Future: Top Cloud Computing Trends Shaping 2024 and Beyond
Explore the upcoming cloud computing trends that will dominate 2024 as the industry undergoes a transformative phase, with businesses projected to invest trillions for groundbreaking innovations. Delve into the key trends shaping the future: AI Transformation through...
Enforcing Security Practices with AWS Config
AWS Config provides a detailed view of your AWS resources, allowing you to see their configuration, relationships, and historical changes. This helps you understand how your resources are interrelated and how they've evolved, promoting better management and...
Config in DevOps
In the ever-evolving world of cloud computing, DevOps teams grapple with managing complex infrastructure while maintaining consistency, compliance, and security. AWS Config emerges as a game-changer, offering a centralized platform to streamline operations, enforce...
The Critical Significance of Cloud Security and Cybersecurity in Nepal
In today's digital age, cloud technology has seamlessly integrated into business operations. The convenience and scalability it offers have led to widespread adoption by companies aiming to streamline processes and boost productivity. Nevertheless, alongside these...
Intrinsic Function and automation in Cloudformation
In this blog, let’s think about the employee onboarding process. Suppose we have 100 new recruits. A sysadmin usually has to do a lot to onboard the employee. One of the onboarding tasks are giving them access to the cloud resources they require. So in Terms of AWS,...
Cloudformation guard
Policy as Code automates enforcement and implementation via the policy to find out logical inconsistencies , syntax error, missing dependencies before they go into the Infrastructure Provisioning process through the IAC. They act as guardrails and are proven to be...
Cyber Security in Nepal
In today's interconnected world, where information flows seamlessly across borders and technology permeates every aspect of life, cybersecurity serves as an essential shield against emerging threats. Nestled in the heart of South Asia, Nepal is rapidly embracing...
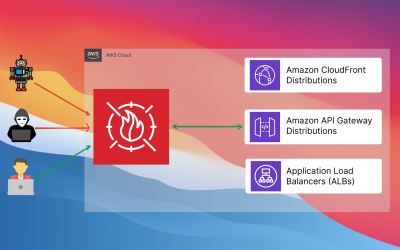
Integrating AWS WAF with Other AWS Services for Comprehensive Web Security
Introduction In the modern digital landscape, safeguarding web applications from multiple threats is paramount. AWS Web Application Firewall (WAF) emerges as a formidable shield against common web exploits such as SQL injection and cross-site scripting (XSS). However,...
Bridging the Technological Gap: Cloud Computing in Nepal
Cloud computing, a groundbreaking technological innovation, is expected to revolutionize Nepal's emerging economy. At its core, cloud computing empowers individuals and businesses throughout Nepal, offering them convenient access to software, hardware, and a wealth of...
 Finland
Finland Bangladesh
Bangladesh