In today’s digital world, keeping our information safe is really important. AWS Key Management Service (KMS) helps us do that by providing a way to lock up our data so that only authorized people can access it. It’s like having a special lock for our digital stuff. With KMS, we can keep our data safe from unauthorized access, who might try to steal it. This introduction will show you how to use AWS KMS to lock up and unlock your data, making sure it stays safe and secure.
In this blog post, we’ll demonstrate how to use KMS to encrypt and decrypt data. We will cover the entire process, including how to create customer managed symmetric keys in KMS, generate a data key and use it to encrypt and decrypt data, how to configure EC2 instance, create a small size file in EC2 instance, encrypt the content inside the file and how to decrypt the encrypted content.
- First of all we will start by creating Customer managed keys in KMS, for this go to the Key Management Service (KMS) console and click on “Create key”.
- At step 1 select the type of key and key usage.
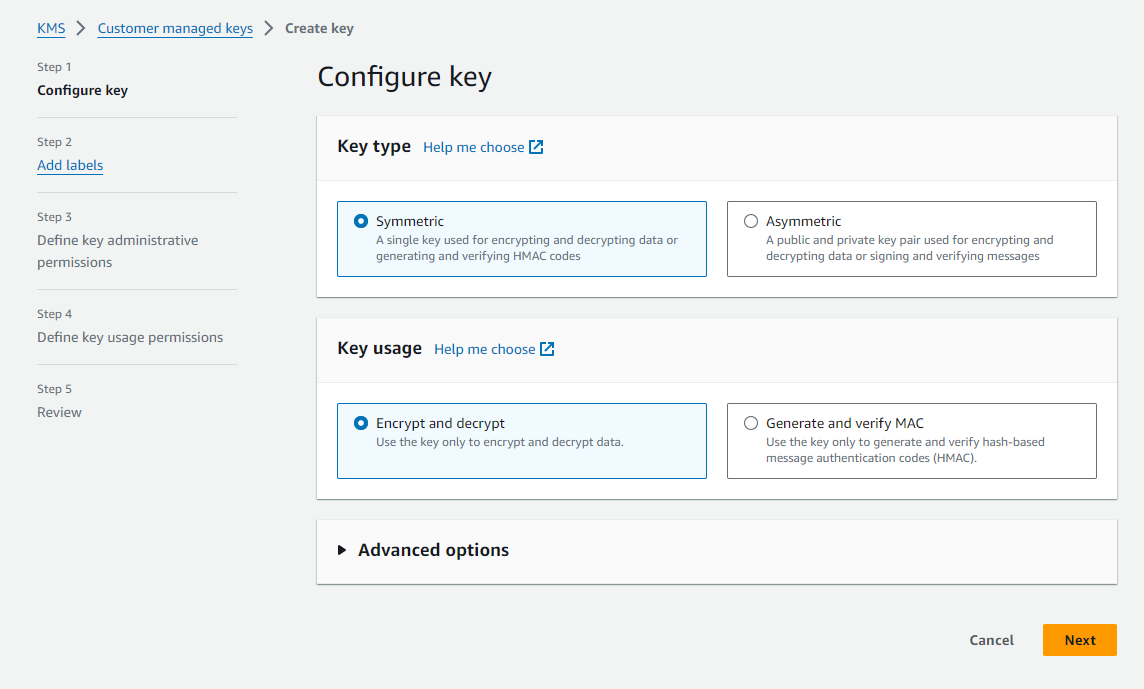
3. At step 2, fill in the Labels of Alias.
4. At step 3, define key administrative permission by clicking the user to whom the permission is to be given including the key deletion permission.
5. At step 4, Select the IAM users and roles that can use the KMS key in cryptographic operations.
6. At step 5 inside the Create Key operation, review all the details filled up and click on “Finish”
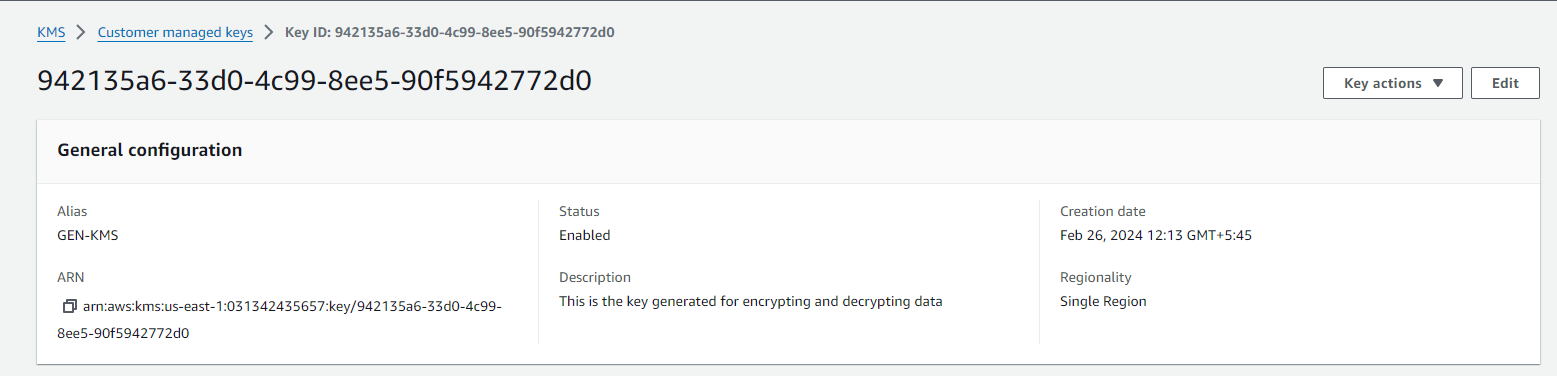
KMS Key details:
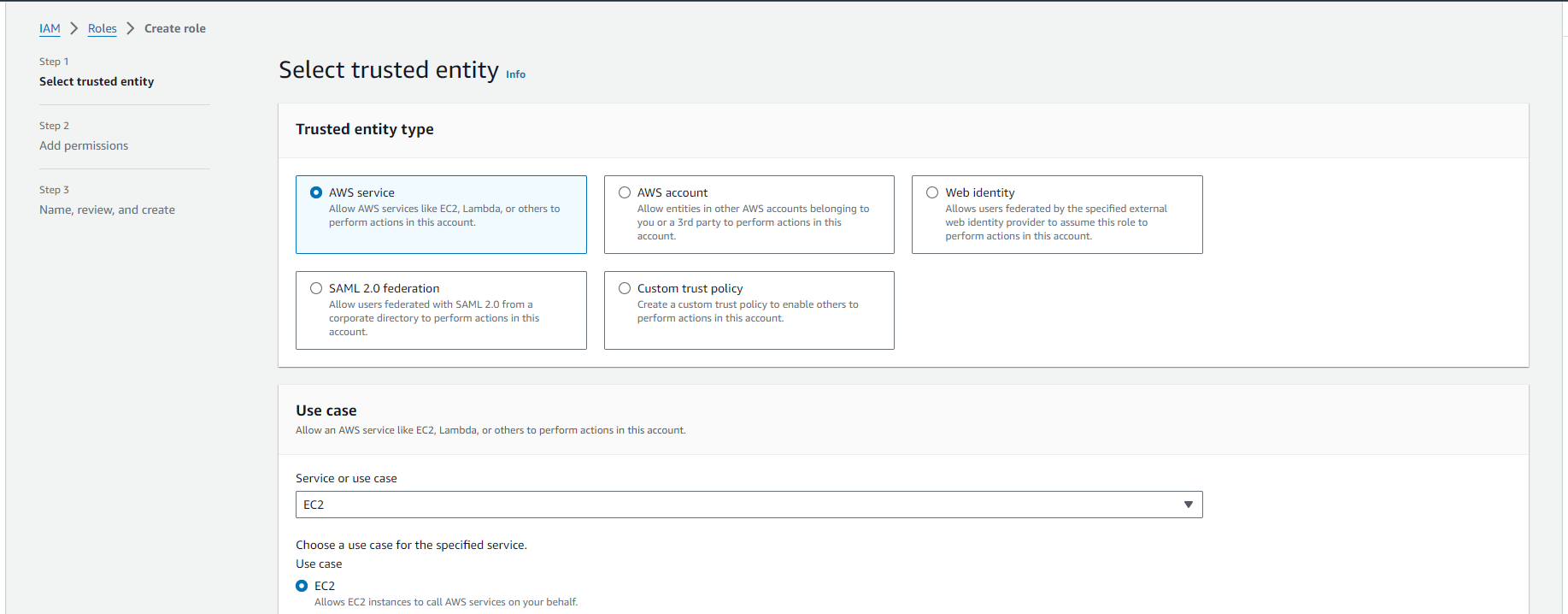
7. Go to the Identity and Access Management(IAM) dashboard and Click on the “Roles” located on the left side of the console.
8. Click on “ Create Role” and in Step 1 select the trusted entity in Use case select EC2 and click on Next.
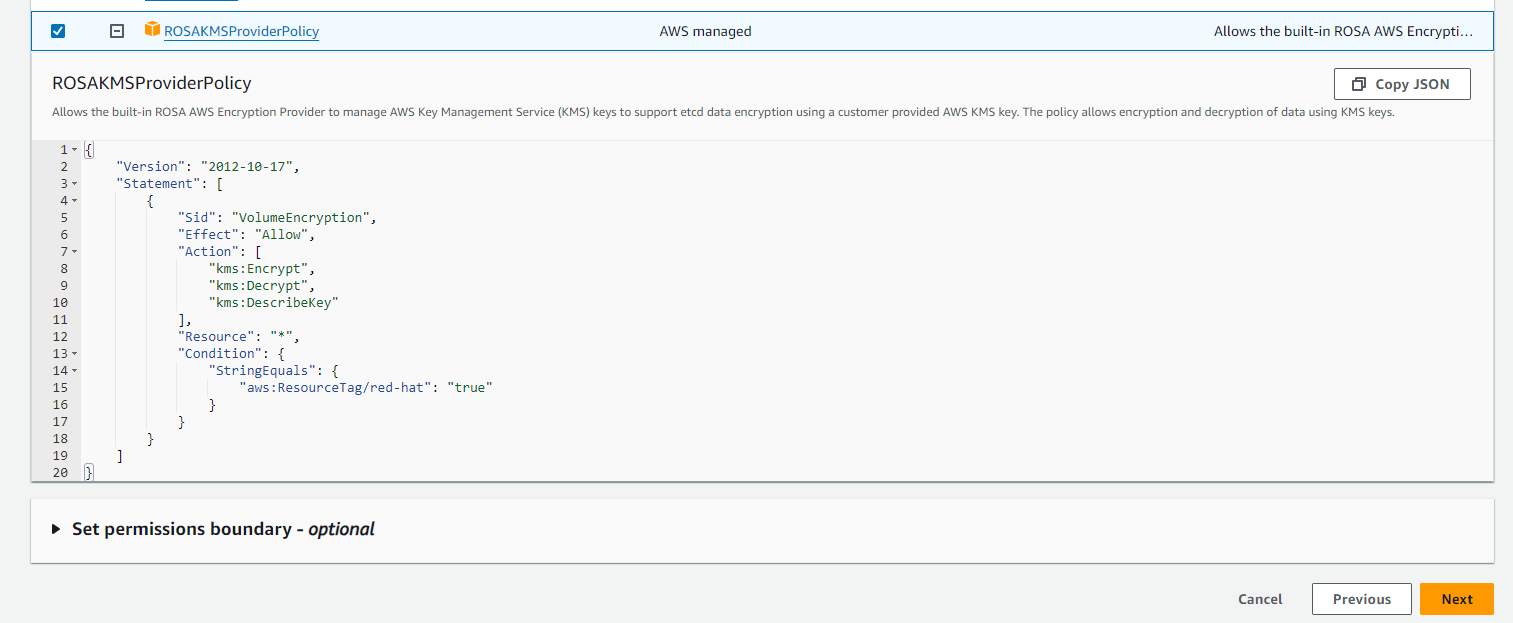
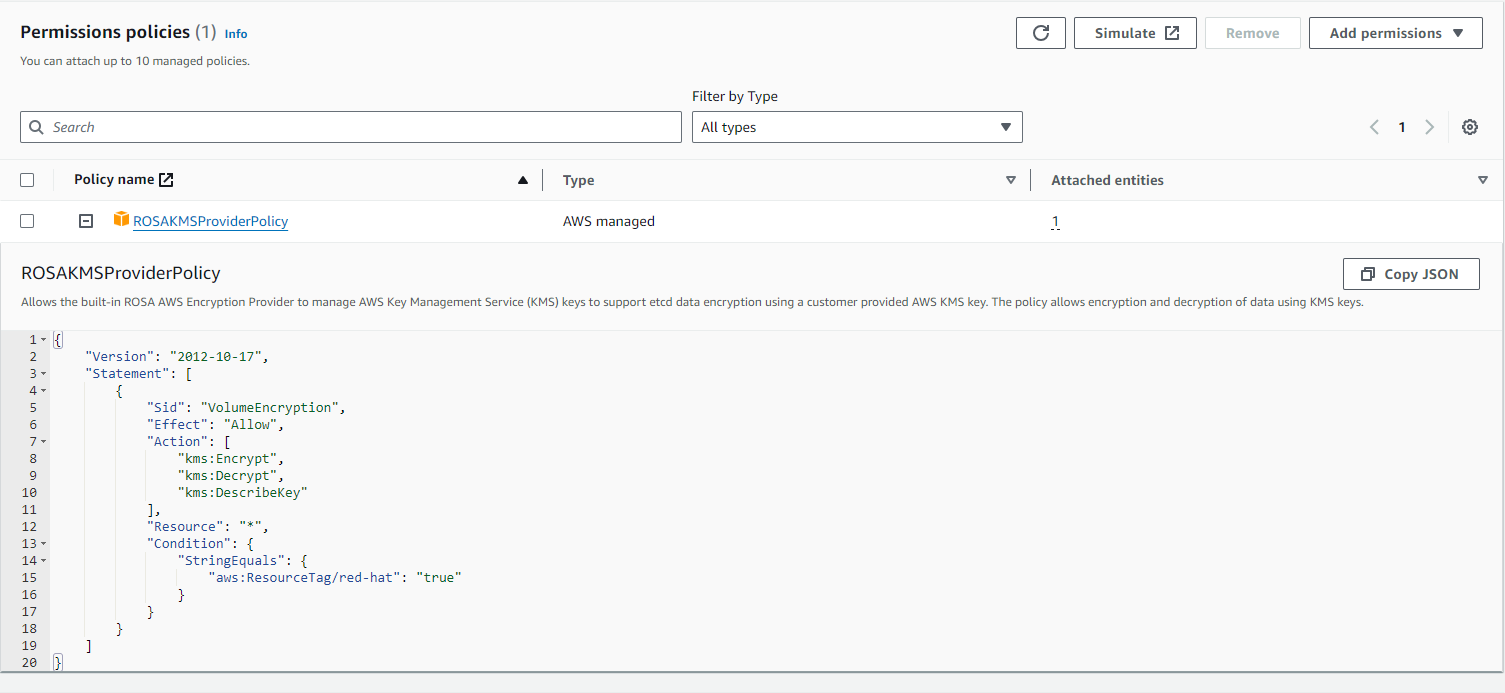
9. In step 2, Choose a policy to attach to your new role. Click on the AWS managed policy named “ROSAKMSProviderPolicy” and click on Next.
10. In step 3, give a name to your role and click on “create role”.
11. Create an EC2 Instance according to your requirements and attach the Role created above to the Instance.
Note: You can use the EC2 instance already created.
EC2 Instance Details:
IAM Role association:
12. Connect to the EC2 instance and follow the following procedure:
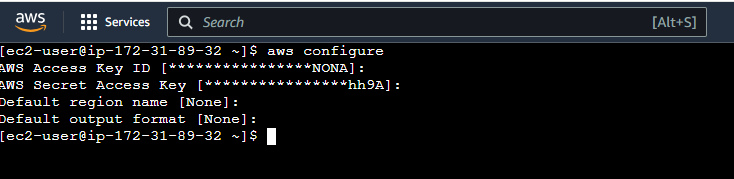
a. Configure AWS CLI in your EC2 instance just as shown below.
b. Create a small text file by giving the command “nano filename.txt” (Replace filename with your desired file name) and add the text that needs to be encrypted.
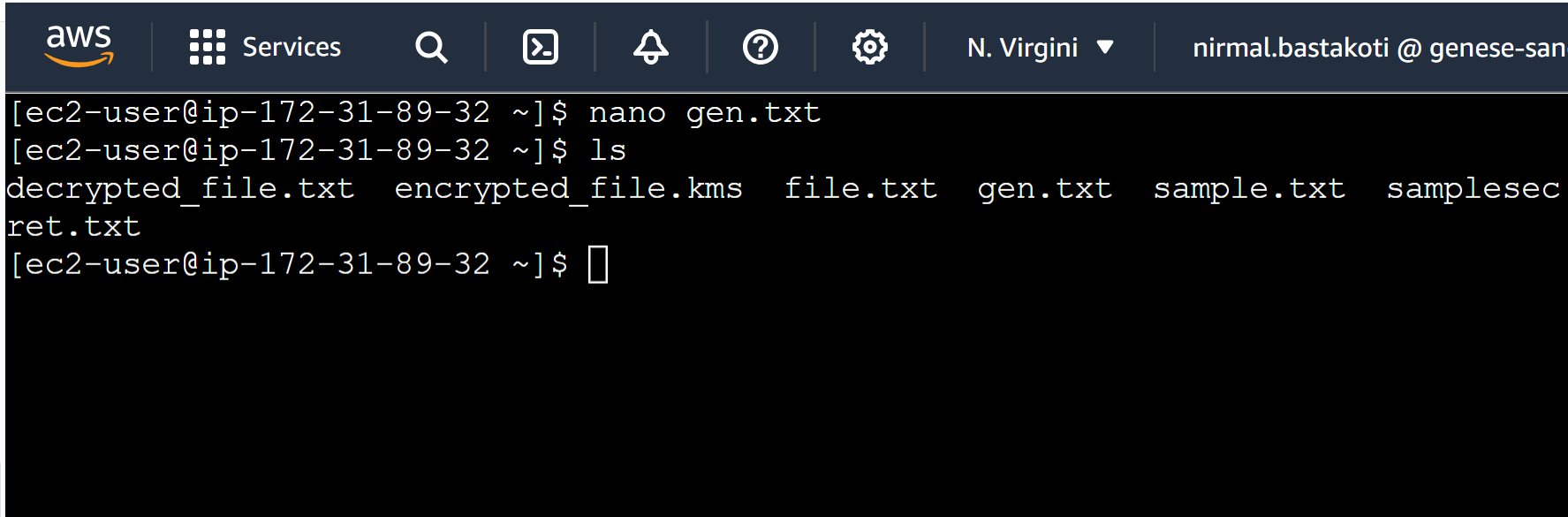
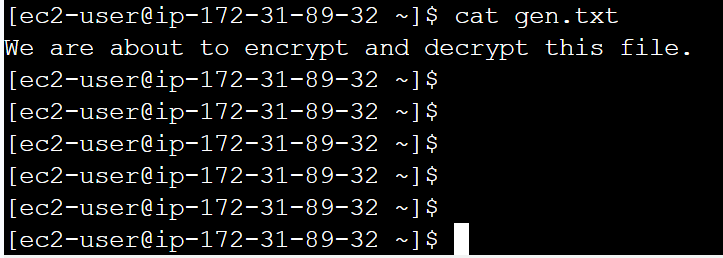
Encryption Process for the created file:
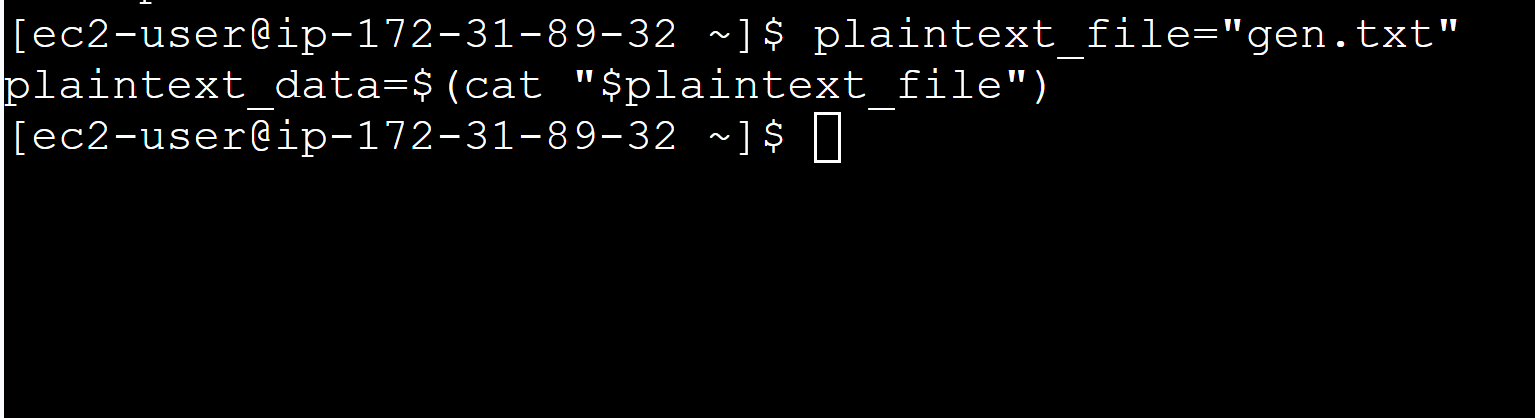
c. To read the file content use the following command:
plaintext_file=”filemane.txt”
plaintext_data=$(cat “$plaintext_file”)
Replace “filename with your file name created earlier”
Base64 encoding is necessary before encryption because encryption algorithms typically work with text data, while files are binary data. Base64 encoding converts binary data into ASCII text format, ensuring compatibility with encryption algorithms that expect text input.
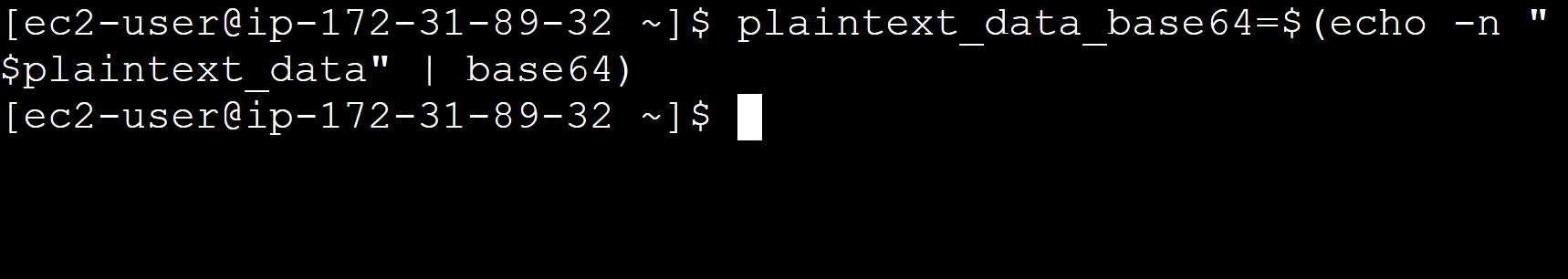
d. For Base64 encoding the file content use the following command:
plaintext_data_base64=$(echo -n “$plaintext_data” | base64)
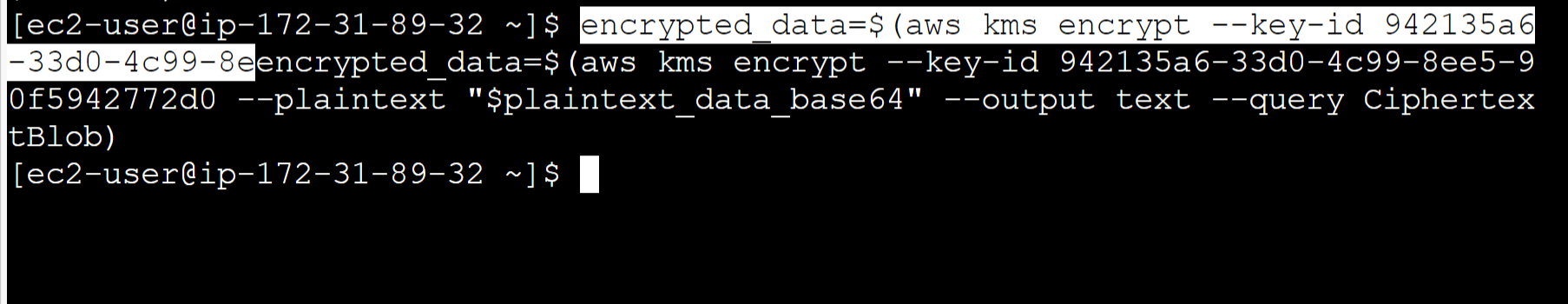
e. To encrypt the file content use the following command:
encrypted_data=$(aws kms encrypt –key-id <key-id> –plaintext “$plaintext_data_base64” –output text –query CiphertextBlob)
replace <Key-id> with the ID of the customer-managed key that we have created earlier.
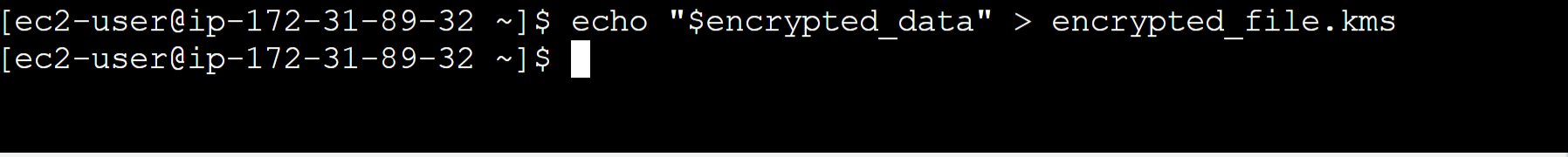
f. We have to save the encrypted data in a file. To save the encrypted date to a file use the following command:
echo “$encrypted_data” > encrypted_file.kms
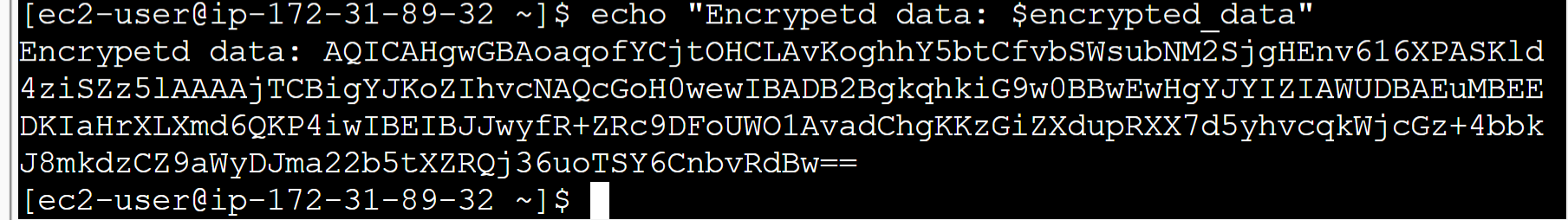
To view the encrypted data:
echo “Encrypetd data: $encrypted_data”
For the Decryption process:
g. Read encrypted data from the file by using the following command:
encrypted_data=$(cat encrypted_file.kms)
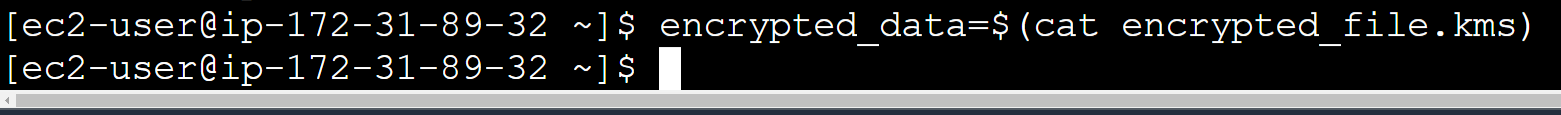
h. To decrypt the data use the following command:
decrypted_data_base64=$(aws kms decrypt –ciphertext-blob “$encrypted_data” –output text –query Plaintext)
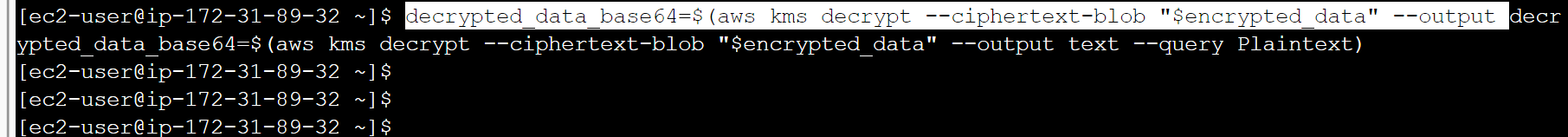
i. To decode the base64 encoded data following command can be used:
decrypted_data=$(echo -n “$decrypted_data_base64” | base64 –decode)
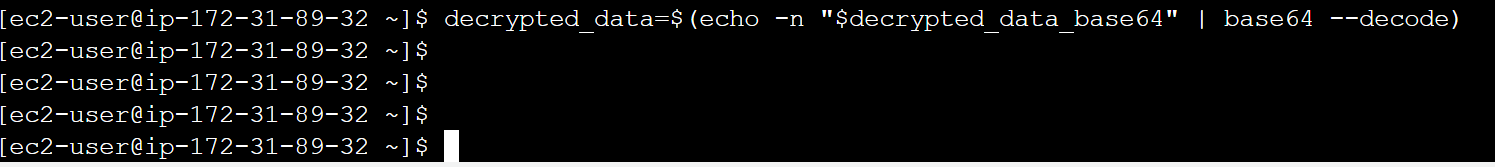
j. We have to save the decrypted data to a file, for which we can use the following command:
echo “$decrypted_data” > decrypted_file.txt
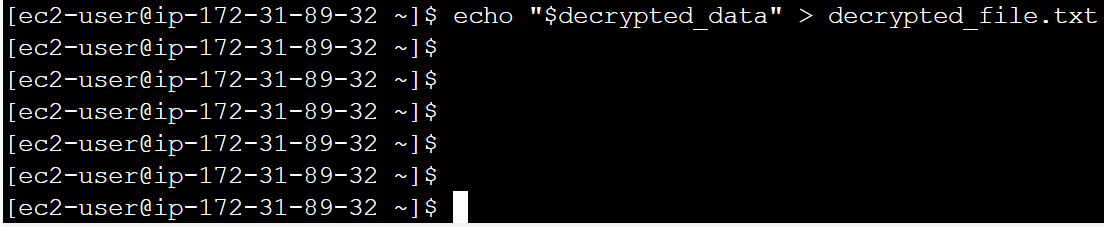
k. To view the decrypted data following command can be used:
echo “Decrypted data: $decrypted_data”
In conclusion, AWS Key Management Service (KMS) provides a robust and secure solution for encrypting and decrypting data in the AWS Cloud. By leveraging KMS, users can create and manage cryptographic keys to safeguard their sensitive information, ensuring that only authorized users have access to the data.
 Finland
Finland Bangladesh
Bangladesh
