Source: AWS
What is AWS Network Firewall and Why is it used?
Cyberattacks are increasing daily, so it is essential to protect your application with a firewall. Network Firewall facilitates meeting the network protection and provides preventative measures. Third-party applications, like Cisco can also meet security requirements but their initial setup cost can be expensive and difficult. An AWS Network Firewall is a low-cost alternative. AWS Network Firewall is a well-fitted decision if you’re on a limited budget and searching for convenient yet defensive network measurements.
As most of the emerging businesses look for security to protect their infrastructure to the enterprise, AWS Network Firewall is a perfect fit.
Firewalls are the most helpful security and compliant tools. Firewalls prevent unauthorised access to networks on which sensitive data is stored, making them a wise tool to comply with regulations and standards.
AWS Network Firewall is a managed service that is easy to set up and scales automatically with network traffic. It filters unwanted and unauthorised traffic into and out of VPCs. AWS Network Firewall is one of several firewalls available on the AWS platform, including Security Groups, Network Access Control Lists, and the AWS Web Application Firewall.
AWS Network Firewall Deployment Models
First, let’s discuss how the firewall works in the Network Architecture. Simply, network traffic to the VPC is routed to a firewall end-point to be monitored before it enters or exits the network.
AWS Network Firewall supports three types of deployment models, based on the use cases:
- Distributed model
- Centralized model
- Combined (hybrid) model
Combined and Centralized model both support VPC to VPC traffic flow using AWS Transit Gateway whereas the distributed model doesn’t require AWS Transit Gateway. In contrast to distributed model, every AWS VPC can have its own AWS Network Firewall, which means it can have a different set of rules for each one. But the distributed model doesn’t support VPC to on-premises connection or network flow. A centralized deployment model uses a centralized VPC into which one or more firewall subnets are deployed.
Architecture Diagram
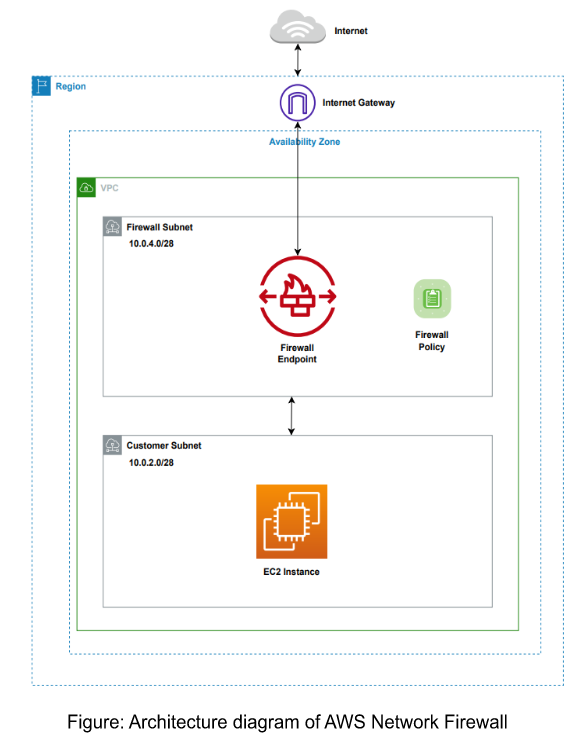
Source:AWS
In this architecture diagram, an additional layer of security to the infrastructure is added. The traffic is filtered on both ways through the Network Firewall. A firewall policy is defined that includes a set of rules to be followed while filtering the traffic.
AWS Network Firewall vs. Security Groups and NACLs
AWS Network Firewall is one of several firewall services available on AWS.
Security Groups
Security Groups are stateful and act as virtual firewalls that filter traffic to Elastic Network Interfaces typically used with EC2 instances. With Security Groups, users can ensure that all the traffic that flows at the instance level is only through the established ports and protocols.
Network Access Control Lists(NACLs)
Network Access Control Lists are stateless firewalls associated with one or more subnets within a VPC. It acts as an optional layer of security that acts as a firewall for monitoring and controlling traffic in and out of the subnet.
Central Management with Firewall Manager
AWS Firewall manager is a service that provides one place to manage all protective controls on AWS. This includes AWS Security Groups, AWS Web Application Firewall, AWS Shield Advanced, and AWS Network Firewall. With AWS Firewall Manager, we can continuously manage and audit user controls across all of the user accounts on AWS.
Guide to provisioning AWS Firewall Network.
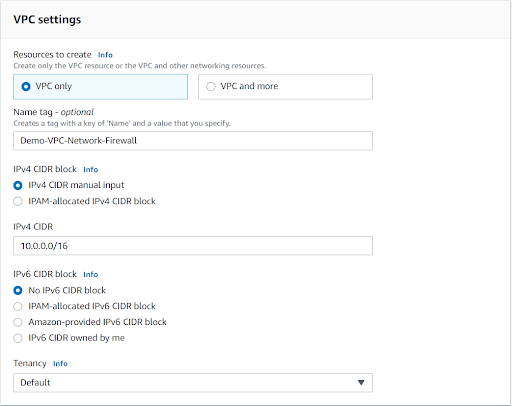
Create a new VPC.
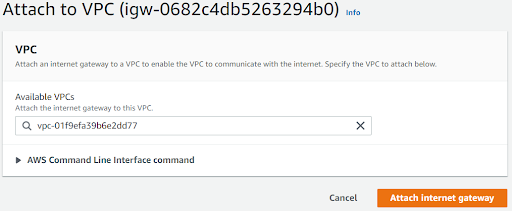
Create an Internet Gateway and attach it to our VPC.
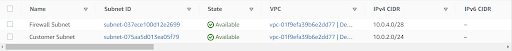
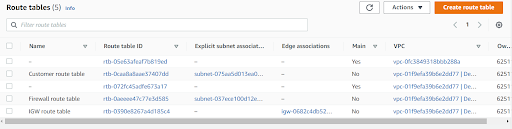
Now Associate the Route tables to the corresponding Subnets.
- Customer Route Table with Customer Subnet
- Firewall Route Table with Firewall Subnet
- IGW Route table with IGW itself on edge association
Select Create Network Rule policy.
Here, there are two Rule Groups:
Stateless rules
In this rule, traffic is evaluated whenever the traffic comes into the subnet. But it won’t be evaluated when traffic comes out from the subnet.
Stateful rules
The traffic will be evaluated in both directions.
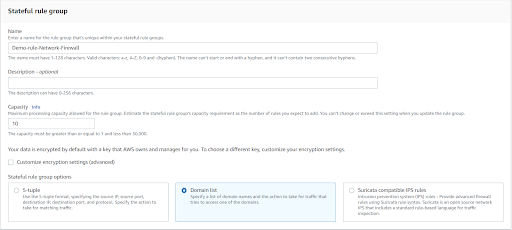
Provide the domain name of the website to which we need to block the traffic

The Network Firewall rule group is created.
Now, let’s create a firewall policy.
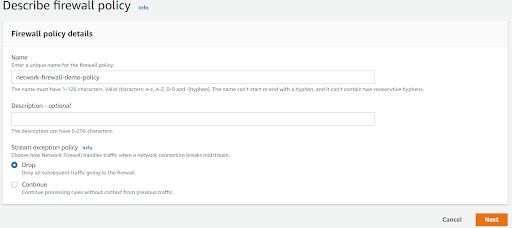
In Add rule Groups, scroll down to the stateful group section, select the Stateful Rule And click Add Rule Groups.
Select Next, Again Next. Finally, create the Network policy.
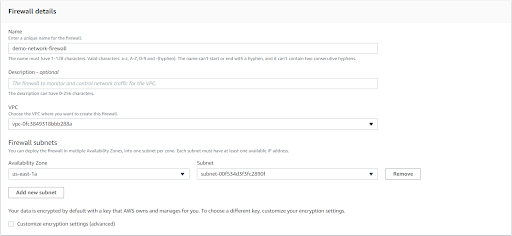
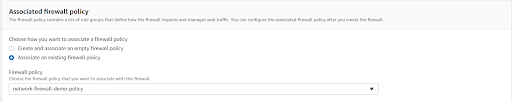
Select the Associate an Existing Firewall policy radio button and select your Network policy.
Now let’s add routes on the Firewall route table internet that should go via the IGW.
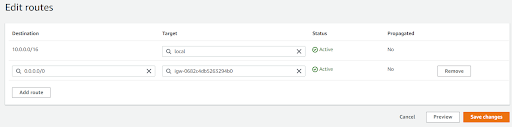
Similarly, let’s add a route on the Customer route table so that traffic for the internet goes via the firewall endpoint.
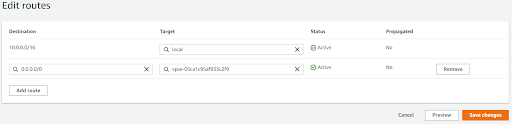
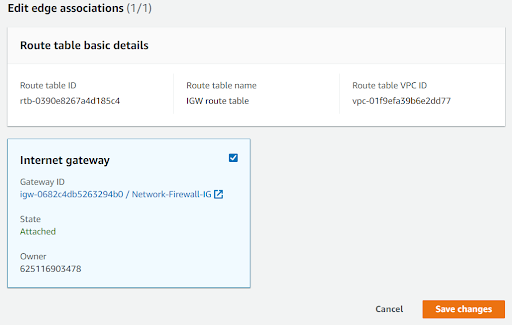
Now let’s associate the IGW route table. Also, add a route for traffic that goes to the customer subnet to route via the firewall endpoint.
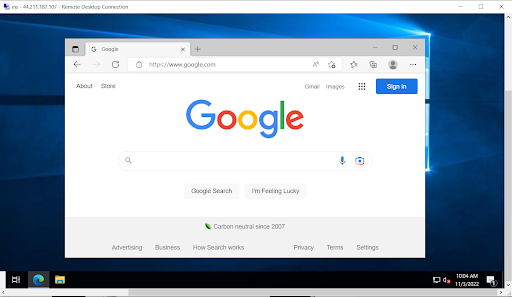
Let’s access www.google.com. And it is working.
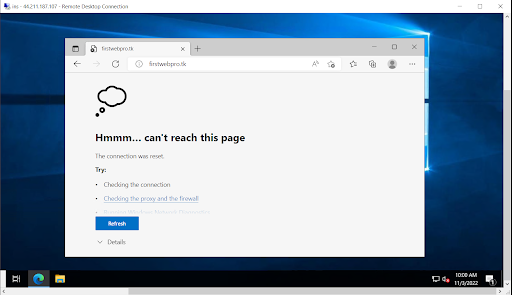
Let’s check the domain that we blocked in our firewall.
Conclusion
In this blog, AWS Network Firewall is created and it adds an additional layer of security to our infrastructure. The traffic is filtered on both ways through the firewall. The firewall policy is also created to define a set of rules to be followed while filtering the traffic.
 Finland
Finland Bangladesh
Bangladesh