Introduction
DevSecOps is a software development methodology integrating security practices into the entire software development lifecycle (SDLC). It stands for Development, Security, and Operations. This approach ensures that security is not an afterthought but an integral part of the software development process.
Evolution of Software Development Methodologies
We’ve come a long way from the Waterfall model, where software was developed with predefined client requirements. Despite being simple and easy to implement, adapting to changes with evolving technologies was challenging for long-running projects.
To address this, we adopted the Agile methodology, which is iterative and flexible to the dynamic requirements of modern software. However, a key challenge persisted: the Development and Operations teams continued to work in silos. Products were tested in developers’ systems but not in production (or production-like) servers.
Then came DevOps, an extension of the Agile model. DevOps made operations agile by integrating them into the development lifecycle, enabling continuous feature development, integration, and delivery to clients.
Yet, one piece remained missing in the puzzle: ensuring the security of the software being developed.
Why DevSecOps?
Although DevOps broke down silos between Development and Operations teams, Security still existed in isolation. Viewing security as an afterthought leads to several risks:
- Delayed Detection: Discovering vulnerabilities only after the application is in production can be catastrophic.
- Inadequate Testing: Conducting security assessments before releases is often impractical for fast-paced Agile sprints.
- Bottlenecks: Integrating security as an add-on disrupts agile workflows, creating delays and increasing the likelihood of delivering insecure software.
By contrast, DevSecOps integrates security throughout the development process, ensuring that software is secure without slowing down delivery.
Transformation: From DevOps to DevSecOps
If your organization already follows DevOps practices, you are well-positioned to implement DevSecOps. Think of DevOps as a prerequisite for DevSecOps, with security practices introduced across the development lifecycle.
However, this transformation requires cultural shifts and must be introduced gradually to avoid overwhelming teams. The transition can be divided into two stages:
- Introducing security tools and practices into the development process
- Making security practices iterative
Building a DevSecOps foundation might take a few months, but once established, it becomes a go-to framework for securing software during development.
For instance, if you’re using AWS CodePipeline, security tools can be integrated into the DevOps pipeline to create a DevSecOps workflow.
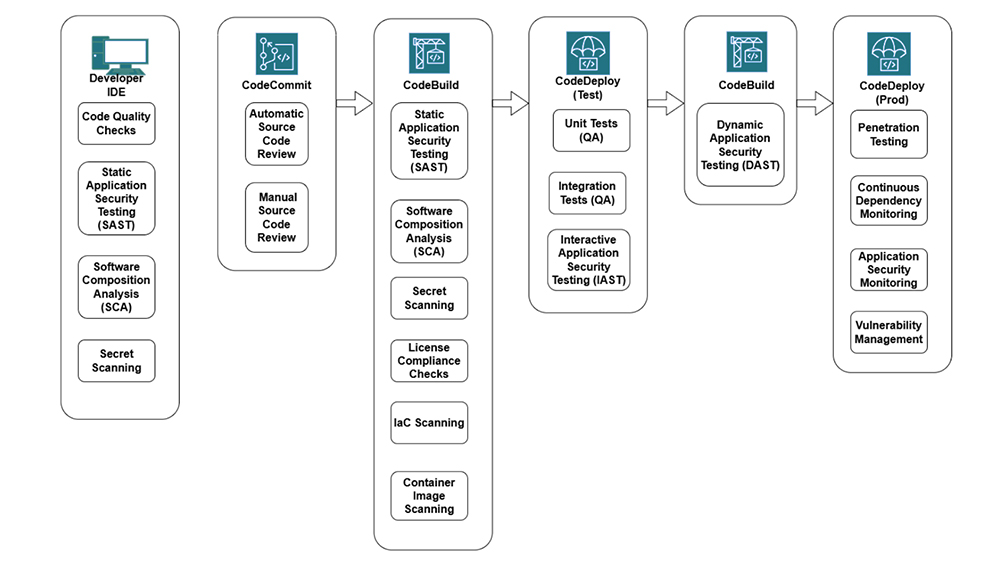
Automated Security Testing
DevSecOps aims to ensure secure software development without slowing down delivery. Most security checks in the DevSecOps lifecycle can be automated, such as:
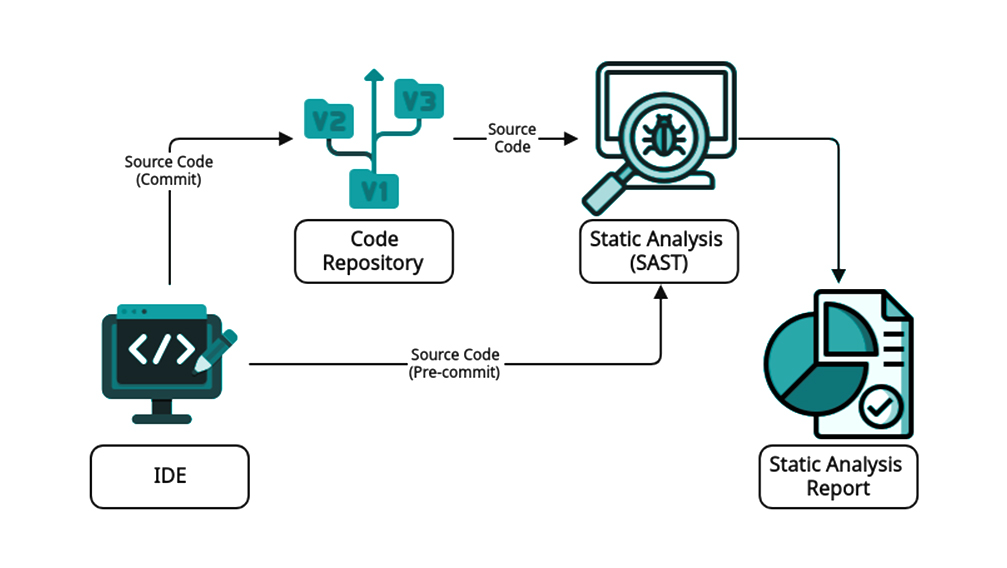
1.Static Application Security Testing (SAST)
SAST tools analyze source code to identify vulnerabilities like XSS, SQL injection, and CSRF, which attackers can exploit. These tools are excellent at catching low-hanging fruits.
2. Dynamic Application Security Testing (DAST)
Some vulnerabilities only surface when an application is running. DAST tools simulate attackers’ behavior to detect such vulnerabilities. Like SAST tools, they should not replace penetration testing but are valuable for identifying common issues.

3. Software Composition Analysis (SCA)
Open-source libraries can introduce vulnerabilities into your codebase. SCA tools analyze third-party dependencies to identify potential security risks.
4. Secret Scanning
Developers sometimes hardcode API keys or secrets during development, which can accidentally make it to production. Tools like secret scanners help identify such hardcoded credentials, preventing incidents like Uber’s 2016 data breach due to exposed Amazon S3 credentials.
Other automated checks include:
- Open-source license compliance
- Infrastructure-as-Code (IaC) scanning
- Container vulnerability scanning
- Continuous dependency monitoring
These tools can be installed in developers’ IDEs or CI/CD pipelines, enabling continuous security testing while maintaining agility.
5. Runtime Application Self-Protection (RASP)
RASP is a security technology integrated directly into an application to detect and prevent real-time attacks. Unlike external security tools, RASP monitors the application’s behavior and neutralizes threats such as SQL injection or XSS during runtime.
Introducing Security Practices
Beyond tools, DevSecOps requires cultural shifts. Security must become a core consideration in planning and design stages. Key practices include:
- Risk Assessment and Threat Modeling: Identify potential risks and exploit scenarios early, even before development starts.
- Secure Coding Practices: Train developers on secure coding techniques tailored to their roles.
- Tailored Security Training: Equip teams with knowledge about specific vulnerabilities relevant to their projects.
The DevSecOps Lifecycle
Once security tools are configured and the team embraces a shared responsibility for security, the software development process can incorporate iterative security practices. Widely adopted frameworks like Microsoft SDL, NIST SSDF, and OWASP DSOMM provide guidelines for building a DevSecOps lifecycle.
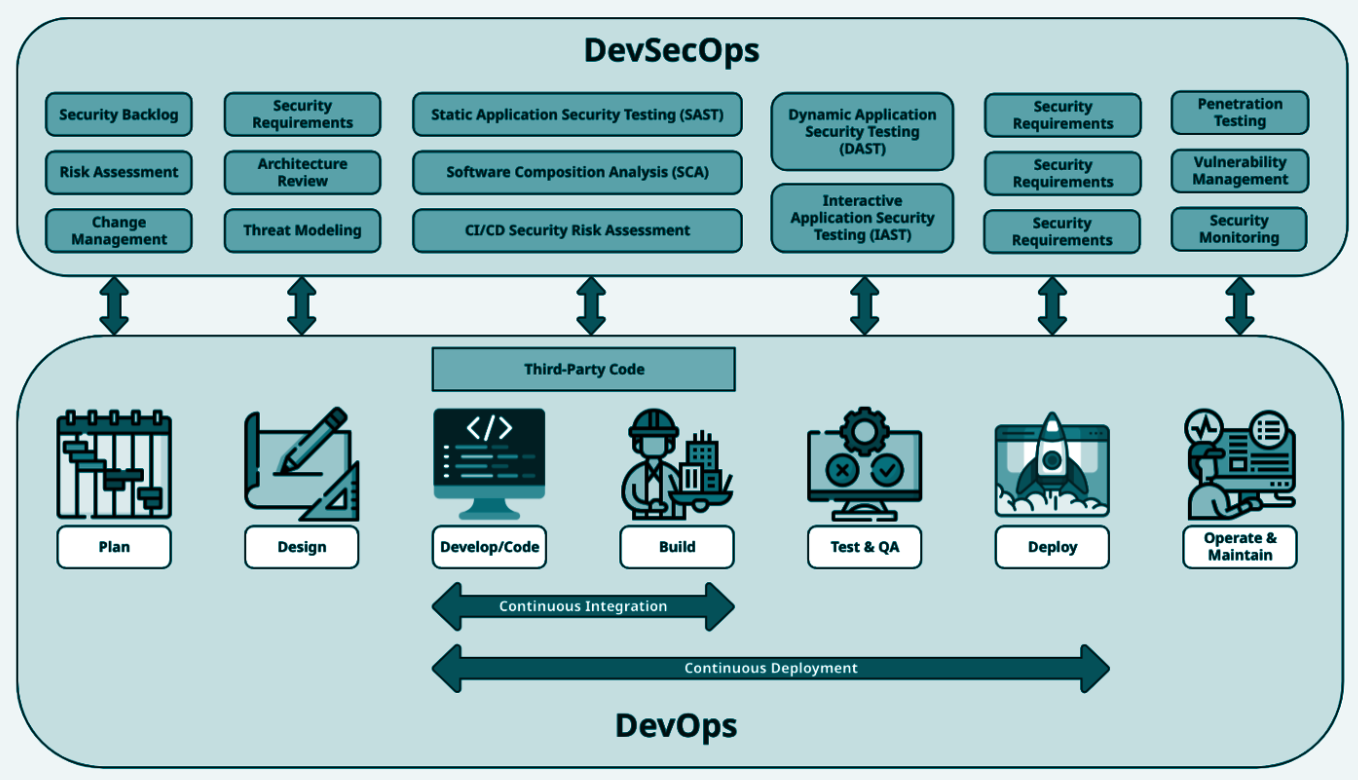
Stage 1: Plan
Create security backlogs alongside functional requirements. Tools and assessments will help refine security priorities over time.
Stage 2: Design
Perform architectural reviews and threat modeling to identify design flaws and potential threats.
Stage 3: Develop / Code
Configure security tools in developers’ environments to detect issues like hardcoded secrets or insecure code during development.
Stage 4: Build
Integrate SAST, SCA, and secret scanners into CI/CD pipelines to analyze code and dependencies. Configure quality gates to block builds for high-severity issues.
Stage 5: Test & QA
Use DAST tools to test the running application for functional and security vulnerabilities.
Stage 6: Deploy
Use infrastructure vulnerability scanners to detect misconfigurations in the deployment environment.
Stage 7: Operate and Maintain
Run periodic assessments and penetration tests for long-running applications. Continuously monitor security events and anomalies in user behavior to identify emerging threats.
Conclusion
DevSecOps is a transformative approach that redefines how security is embedded into software development. By integrating security practices throughout the SDLC, organizations can deliver robust, secure, and resilient applications. Embracing DevSecOps requires technological and cultural shifts, with buy-in from all stakeholders. Investing in the right tools, training, and processes ensures the software development lifecycle remains agile and secure.
Start integrating security into your development lifecycle today to build applications that are not only functional but also resilient against emerging threats.
 Finland
Finland Bangladesh
Bangladesh
