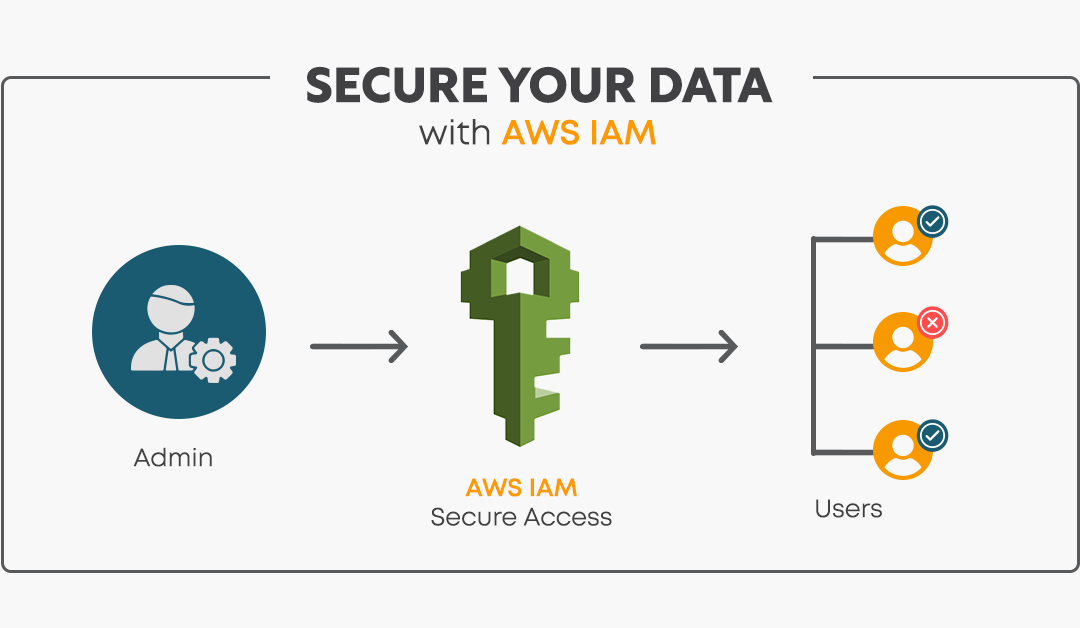
In the era of cloud computing, managing access to resources is critical to ensuring the security and efficiency of your infrastructure. AWS Identity and Access Management (IAM) serves as the cornerstone for controlling access to AWS services and resources. While IAM provides powerful tools for defining permissions and securing the environment, improper configurations or neglected best practices can lead to vulnerabilities and unauthorized access.
At Genese Solution, we specialize in helping businesses secure their cloud environments through robust IAM strategies tailored to their unique needs. With years of experience delivering secure, scalable, and compliant AWS solutions, we’ve seen firsthand how effective IAM practices can transform an organization’s security posture.
This blog delves into the best practices for AWS IAM security, offering actionable insights to help you safeguard your cloud environment. Whether you’re a seasoned AWS user or just starting your journey, implementing these strategies will empower you to maintain a secure, compliant, and well-managed AWS setup.
Understanding IAM
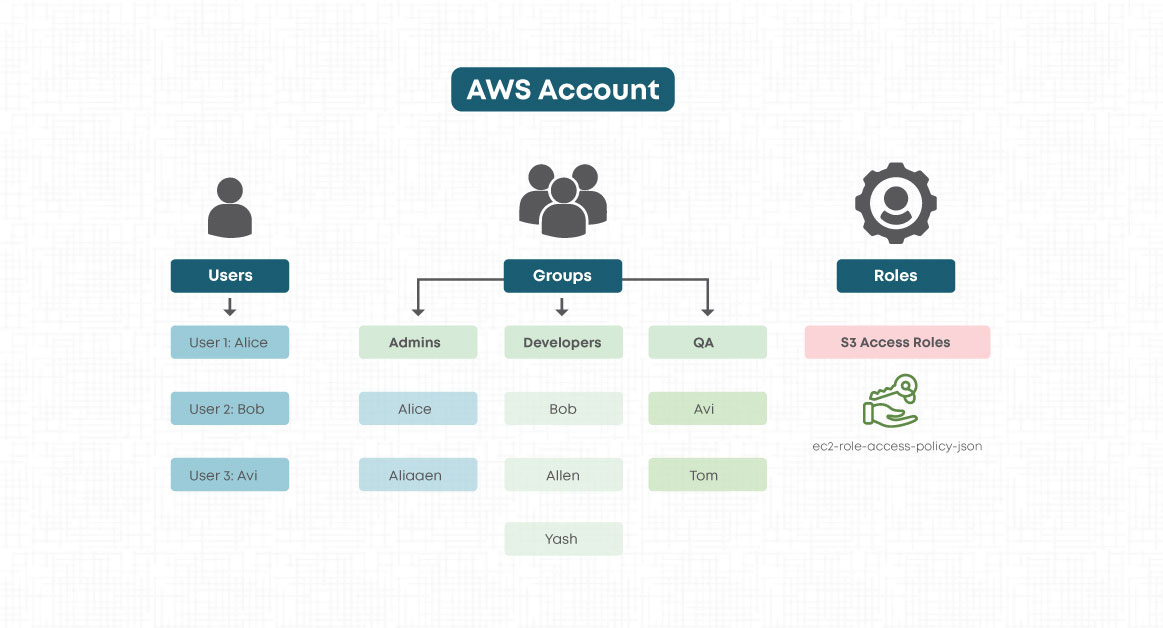
AWS Identity and Access Management (IAM) is a web service that helps to control access to AWS resources securely. We use IAM to control who is authenticated (signed in) and authorized (has permissions) to use resources. The granularity defined in the IAM configuration is critical for protecting the resources and data. Below are some of the best practices to follow for robust IAM security:
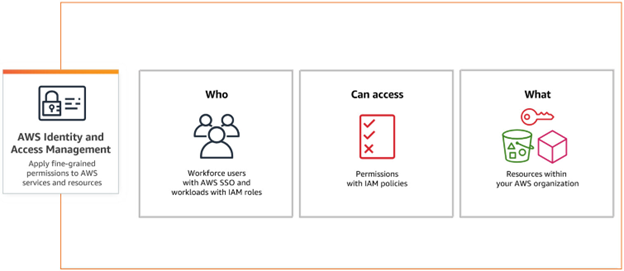
Best Practices:
1.Secure Your Root Account
The root account has access to every resource and every feature. This, if it gets to the user with malicious intent, can be used to destroy or alter the existing data and infrastructure. It is not advised to perform any activities from the root account except for the initial setup tasks. Instead, an IAM user should be created and the daily operations should be performed from that account.
The root account should always have the most security, with MFA and strong password protection. MFA should be enabled for all IAM users, specifically those with administrative access. The root accounts should compulsorily have MFA. Apps like Google Authenticator can be used for this purpose.
Our Practices: At Genese Solution, for every customer’s AWS account we have implemented MFA for all root and IAM user accounts, significantly reducing the risk of unauthorized access. This is part of a broader strategy to meet stringent compliance requirements. We also ensure that the root account has a strong, unique password that is changed periodically. In order to limit the Root user activities, we also have Service control policies in place that restrict root users from performing any activities
2.Principle of Least Privilege
A user, group, or role should only be given privileges enough to perform their job or function. This minimizes the potential impact of compromised credentials. If the AWS-managed policies have more than the required permissions, create a custom policy according to your own requirements. For example: a person from the finance department, who is in charge of billing, does not require write access to other resources except for the cost and billing section.
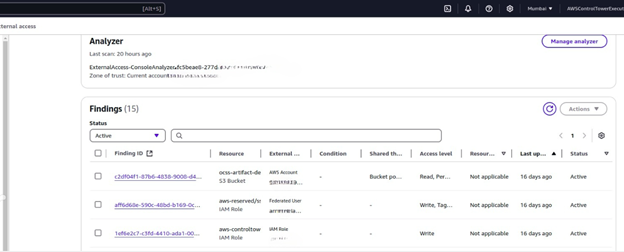
The permissions can be reviewed using the IAM Access Analyzer.
IAM Access Analyzer is designed to help identify and analyze resource access in the AWS environment. It automatically reviews resource-based policies (like those on S3 buckets or KMS keys) to identify unintended public or cross-account access and provides insights into how resources such as IAM roles, S3 buckets, KMS keys, Lambda functions, and more are shared with other AWS accounts, AWS services, or the internet. This is especially useful for ensuring that the AWS environment is secure and meets compliance requirements.
Our Practices: At Genese Solution, for every customer’s AWS account we have implemented MFA for all root and IAM user accounts, significantly reducing the risk of unauthorized access. This is part of a broader strategy to meet stringent compliance requirements. We also ensure that the root account has a strong, unique password that is changed periodically. In order to limit the Root user activities, we also have Service control policies in place that restrict root users from performing any activities
3.Use Roles Instead of Users for Access
Roles create temporary credentials whose expiration time can be configured during their creation. Since they are valid only for a certain period of time, it minimizes the exposure risks.
These roles also allow entities from one AWS account to access resources in another without sharing credentials. This simplifies access for AWS services (e.g., an EC2 instance assuming a role to access an S3 bucket).
Roles are also considered more safe and secure since they do not require human intervention for credential management.
Our Practices: At Genese, we enforce the use of roles for Service Access without embedding credentials. For multi-account environments, IAM roles are used instead of sharing IAM user credentials. This approach minimized credential exposure and ensured compliance with HIPAA regulations.
4.Review and Monitor consistently
Any configuration should be reviewed time and again to ensure it remains effective. So, regular security checks should be performed to identify and fix vulnerabilities.
IAM activities should be regularly monitored. This helps recognize the anomaly and the potential security risks faster. Set up alerts for suspicious activity, such as repeated login failures or changes to critical policies.
Our Approach: We establish a continuous monitoring framework using AWS CloudTrail and Amazon CloudWatch. This enabled customers to detect and respond to potential security incidents in real time. We review IAM policies, user roles, and permissions at scheduled intervals. We log all IAM-related activities and monitor them for anomalies, such as unauthorized policy changes or login attempts. We use Amazon CloudWatch and AWS Config to trigger alerts for any security misconfigurations or policy violations.
5.Rotate credentials periodically
Frequently changing a user’s credentials ensures that old access keys are disabled and new keys are securely distributed. This helps limit the time they can be used by an attacker if compromised. By rotating the credentials, you reduce the attack surface.
Our Approach: At Genese Solution, we automate credential rotation using AWS Secrets Manager, which reduces the operational overhead and enhances their security posture. We enforce expiration policies for credentials to ensure they are not left active indefinitely.
6.Ensure Secure Offboarding:
If a former employee or someone with access leaves the organization, their users and access should be immediately revoked with the necessary knowledge transfer.
Our Practices: We have implemented a secure offboarding process by integrating IAM user deactivation with HR systems to ensure timely access revocation and reduce manual intervention. Before deactivation, access and responsibilities are also reassigned to prevent future disruptions.
Why Genese Solution?
At Genese Solution, we bring a wealth of experience in designing and implementing secure AWS environments. Our team of certified AWS experts has helped organizations across industries—from healthcare and finance to e-commerce and manufacturing—achieve their security and compliance goals.
Here’s what sets us apart:
- Proven Track Record: We’ve successfully delivered IAM security solutions for clients with complex, multi-account AWS environments.
- Tailored Strategies: We understand that every organization is unique. Our solutions are customized to meet your specific needs and challenges.
- End-to-End Support: From initial assessment to ongoing monitoring, we provide comprehensive support to ensure your AWS environment remains secure and compliant.
Conclusion
In today’s cloud-driven environment, ensuring robust security for your AWS resources is paramount. By adopting best practices for AWS Identity and Access Management (IAM), you can significantly enhance the protection of your infrastructure and data. From implementing least privilege access to enabling Multi-Factor Authentication (MFA), regular credential rotation, and leveraging IAM roles instead of users, these strategies collectively minimize risks and bolster your security posture.
IAM is not a one-time setup but an ongoing process that requires continuous monitoring, periodic audits, and adapting to evolving security threats. Proactively managing IAM not only safeguards your AWS environment but also ensures compliance with industry standards and fosters trust with your stakeholders. Prioritize IAM security as an integral part of your organization’s cloud strategy to stay resilient in the face of modern security challenges.
Co-Author : Pooja Shrestha
 Finland
Finland Bangladesh
Bangladesh